Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
What is Penetration Testing?
In penetration testing, also known as pen testing, a cyber-security specialist looks for and attempts to take advantage of weaknesses in a computer system. This assault simulation aims to find any vulnerabilities in a system’s defenses that an attacker may exploit.
This is analogous to a bank employing a thief to attempt to get into their building and get to the vault. In the event that the would-be burglar is successful in breaking into the bank or the vault, the bank will have important insight on how they could strengthen their security protocols.
Why is Security Penetration Testing Important?
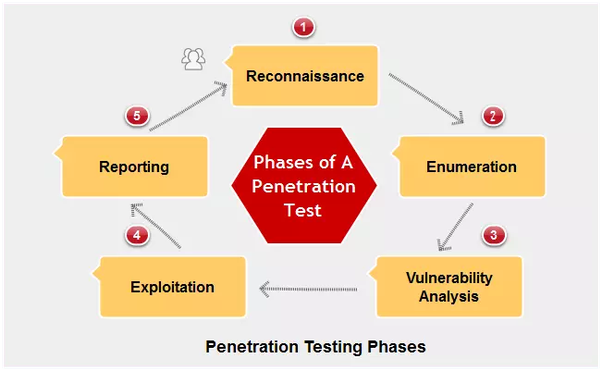
Penetration testing makes an effort to access a system within a company in order to find security flaws. During the test, security personnel should be notified if the system is sufficiently protected. In the absence of it, the system is seen as vulnerable. Penetration testing can therefore aid in enhancing information security procedures.
The ideal way to evaluate an organization’s defenses is to conduct a “blind” penetration test, in which the security and operations teams are kept in the dark about its existence. Even so, the test may function as a security drill that assesses how people, tools, and security procedures interact in an actual setting—even if internal teams are aware of it.
Typically, penetration testing is creative and unstructured. For instance, one test may employ a spear phishing assault on corporate officials, while another test would employ a brute force attack. Because skilled attackers will employ similar abilities and inventiveness to pinpoint the organization’s security flaws, this innovation is crucial.
Penetration testing also has the advantage of being carried out by outside contractors, thus it is feasible to decide how much information about internal systems to provide. A penetration test can mimic both a privileged insider and an external attacker who is unaware of the internal network.
How Penetration Testing Work?
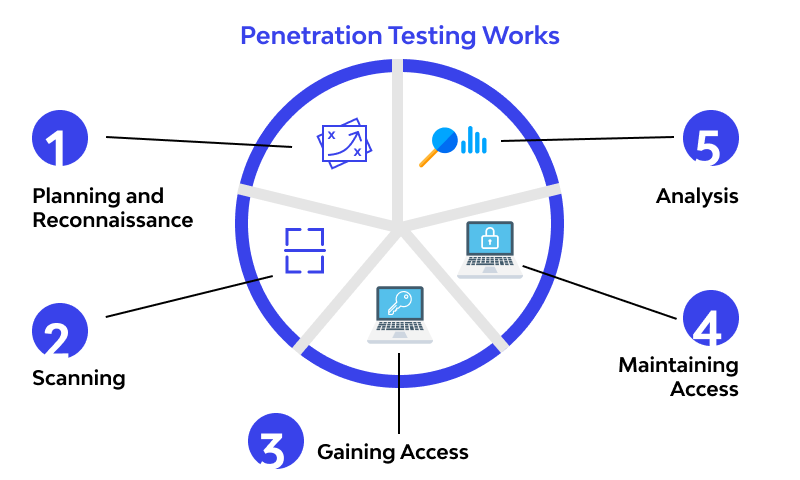
Pen tests begin with a reconnaissance phase, in which an ethical hacker spends time obtaining knowledge and data to help them organize their fictitious assault. After then, obtaining and preserving access to the target system becomes the key priority, necessitating a wide range of techniques.
Programs used to generate SQL injections or brute-force assaults are examples of attack tools. Additionally, there is gear made expressly for pen testing, including small, unnoticeable devices that may be inserted into a networked computer to provide a hacker remote access to the network. Additionally, social engineering methods can be employed by an ethical hacker to identify weaknesses. For instance, posing as delivery personnel to obtain physical entry to the premises or sending phishing emails to staff members of the business.
The final step in the test is for the hacker to conceal their traces, which entails taking out any embedded hardware and taking all other necessary precautions to stay under the radar and leaving the target system exactly as they found it.
What are the types of Penetration Tests?
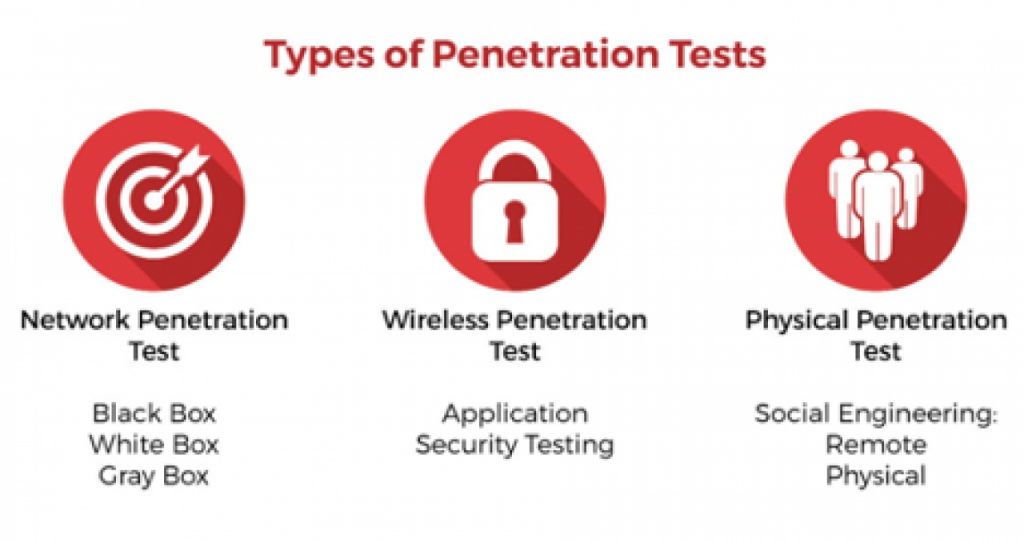
External testing: – External penetration tests aim to compromise a firm’s online assets, such as email and domain name servers (DNS), the corporate website, and the web application itself. Getting access and extracting useful data is the aim.
Internal testing:- An application that is accessible across a firewall is tested internally by a tester who impersonates a hostile insider. It’s not always the same as modeling a renegade employee. An employee whose credentials were compromised by phishing is a typical place to start.
Blind testing:- A tester in a blind test is merely provided with the name of the targeted organization. This provides security workers with an instantaneous view of how an actual application assault would go.
Double-blind testing:- In a double-blind test, often called a covert test or covert test, firms do not provide penetration testers access to security information. Additionally, they keep the testing a secret from their own computer security personnel. Usually, the people in charge of these exams have strict supervision over them.
Targeted testing:- In this case, the security guards and the tester collaborate and communicate with one another about their whereabouts. This is an excellent training exercise that gives a security team instant feedback from the perspective of a hacker.
What are the top Penetration Testing Software & Tools?

1. Netsparker:-
One well-liked automated online program for penetration testing is Netsparker Security Scanner. Everything from SQL injection to cross-site scripting may be detected by the program. This is a tool that developers may use for online apps, web services, and webpages.
The system has sufficient power to simultaneously scan anywhere from 500 to 1000 web apps. With the help of authentication, URL rewriting rules, and attack choices, you can personalize your security scan. Netsparker automatically exploits read-only vulnerabilities. An evidence of exploitation is shown. Vulnerabilities’ effects are immediately visible.
Benefits:
- Examine over a thousand online apps in less than a day!
- Increase the number of team members to facilitate cooperation and simple sharing of results.
- Automatic scanning guarantees that just a minimal setup is required.
- looks for XSS and SQL vulnerabilities in web applications that can be exploited.
- Reports on regulatory compliance and legal web applications.
- Accurate detection is ensured by proof-based scanning technology.
2. Wireshark:
600 writers have contributed to the award-winning network analyzer Wireshark, formerly known as Ethereal 0.2.0. You can easily collect and decipher network packets with this program. The utility is available for several operating systems, including as Windows, Linux, FreeBSD, and Solaris, and is open-source.
Benefits:
- offers choices for both live-capture and offline analysis.
- You may investigate different characteristics, such as source and destination protocols, by capturing data packets.
- It provides the capacity to look at even the smallest details of activity across a network.
- Coloring rules can be added to the pack voluntarily for quick, straightforward examination.
3. Metasploit:
The most popular automated penetration testing framework worldwide is called Metasploit. Professional teams may enhance awareness, keep one step ahead of the opposition, and arm and empower defenders using Metasploit, which also helps manage and validate security assessments.
It is helpful for establishing a defense, identifying vulnerabilities, and assessing security. This program, which is open source software, enables a network administrator to breach security and locate critical vulnerabilities. This tool helps novice hackers hone their abilities. The technology gives social engineers a means to duplicate webpages.
Benefits:
- Simple to use, featuring a command line and GUI clickable interface.
- OWASP vulnerability testing tools include awareness, spear phishing, payloads to circumvent leading solutions, manual brute-forcing, and awareness.
- gathers testing information for more than 1,500 exploits.
- Network segmentation testing using MetaModules.
- This may be used to investigate more recent vulnerabilities in your infrastructure.
- accessible on Linux, Windows, and Mac OS X.
- is applicable to apps, networks, and servers.
4. BeEF:
The greatest use case for this pen testing tool is to examine a web browser. designed to thwart online threats and may prove advantageous for mobile users. The Browser Exploitation Framework, or BeEF, searches GitHub for vulnerabilities. BeEF is meant to look for vulnerabilities outside of the network and client system boundaries. The framework, on the other hand, will examine exploitability in the context of a single source—the web browser.
Benefits:
- Client-side attack vectors are a useful tool for assessing security posture.
- Establishes connections with many web browsers before directing command modules are launched.
5. John The Ripper Password Cracker:
One of the most common weaknesses is passwords. Passwords can be used by attackers to get credentials and access private systems. The most important tool for password cracking is John the Ripper, which offers several systems for the job. The software used for pen testing is open source and free.
Benefits:
- recognizes various password hashes automatically.
- finds password vulnerabilities in databases.
- Hash Suite, Hash Suite Droid, Linux, and Mac OS X all have pro versions available.
- comes with a modifiable cracker.
- enables online documentation exploration for users. A list of the adjustments made between various versions is included in this.
6. Aircrack:
The goal of Aircrack NG is to exploit vulnerabilities in wireless networks by collecting data packets and exporting them as text files for further examination. In 2019, Aircrack received another update, despite appearing to have been abandoned in 2010.
With support for WEP dictionary attacks, this program works on a number of operating systems and platforms. It supports several cards and drivers and provides faster tracking than the majority of other penetration tools. The suite can break into WEP by employing statistical approaches and a password dictionary once it has successfully captured the WPA handshake.
Benefits:
- Compatible with Solaris, Linux, Windows, NetBSD, OpenBSD, and FreeBSD.
- This utility allows you to export data and capture packets.
- It is intended to assess driving capabilities in addition to wifi gadgets.
- concentrates on several aspects of security, including testing, monitoring, cracking, and attacking.
- Attacking techniques include de-authentication, creating fictitious access points, and replay assaults.
7. Acunetix Scanner:
You may do a penetration test using Acutenix, an automated testing tool. The program may audit complex management reports and compliance problems. Numerous network vulnerabilities may be handled by the program. It is even possible for Acunetix to incorporate out-of-band vulnerabilities.
The sophisticated tool works with the widely used WAFs and Issue Trackers. One of the most advanced cross-site scripting and SQL injection testing products available, Acunetix has a high detection rate and offers sophisticated advanced XSS detection.
Benefits:
- The program addresses more than 4500 vulnerabilities, including XSS and SQL injection.
- The Login Sequence Recorder scans password-protected places and is simple to use.
- Black and white box testing are streamlined using AcuSensor Technology, manual penetration tools, and built-in vulnerability management to improve and facilitate repair.
- able to quickly crawl hundreds of thousands of web pages.
- the capacity to operate both locally and via a cloud solution.
8. Burp Suite Pen Tester:
The Burp Suite is available in two editions for developers. The core tools required for scanning operations are included in the free edition. If you want sophisticated penetration testing, you may also choose the second edition. This is the perfect tool for web application security audits. Tools exist for both mapping the tack surface and analyzing browser-to-destination server queries. Most information security experts utilize this industry-standard approach, which leverages Web Penetration Testing on the Java platform.
Benefits:
- possible to compile web apps into an autonomous crawl.
- accessible on Linux, Windows, OS X, and Windows.
9. Ettercap:
The goal of the Ettercap suite is to thwart man-in-the-middle attacks. You will be able to carry out particular operations and create the packets you desire using this program. Invalid frames and more complex strategies can be sent by the software through alternative settings.
Benefits:
- This program is perfect for testing and monitoring LANs, as well as for deep packet sniffing.
- Both active and passive deconstruction of safeguards are supported by Ettercap.
- Content screening may be finished instantly.
- Additionally, the utility offers host and network analysis settings.
10. W3af:
The goal of the W3af web application audit and attack frameworks is to identify and take advantage of weaknesses present in any online application. There are three different kinds of plugins available: attack, audit, and discovery. After that, the program sends these to the audit tool so that it may look for security vulnerabilities.
Benefits:
- Both strong enough for developers and simple enough for novices to utilize.
- It is capable of generating both raw and automated HTTP requests.
- the capacity to set up and operate as an MITM proxy.
What is Penetration testing and web application firewalls?
WAFs and penetration testing are complementary but separate security techniques.
With the exception of blind and double blind tests, the tester will often employ WAF data—such as logs—to identify and take advantage of an application’s vulnerabilities in pen tests.
Pen testing data might also be useful to WAF managers. WAF setups can be modified whenever a test is finished to protect against any weak points that were found.
Lastly, pen testing fulfills a few compliance needs, such as SOC 2 and PCI DSS, for security auditing processes. Only the usage of a certified WAF can satisfy some criteria, including PCI-DSS 6.6. Pen testing’s previously mentioned advantages and capacity to enhance WAF settings mean that doing so doesn’t lessen its usefulness.


“Penetration testing tools are an invaluable asset in the cybersecurity arsenal, empowering organizations to stay ahead of the curve and maintain a vigilant stance against cyber threats.”