Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
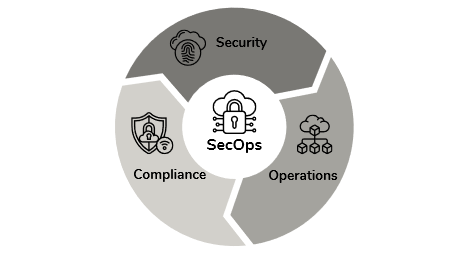
Imagine a bustling city where law enforcement and emergency services work seamlessly together to prevent crime, respond to threats, and keep people safe. Now, think of your organization’s IT infrastructure as that city, and cybersecurity threats as criminals constantly looking for vulnerabilities to exploit. SecOps (Security Operations) acts as the security force of your digital environment, ensuring that security is not an afterthought but a core part of IT operations.
SecOps is a strategic approach that merges security practices with IT operations, creating a continuous, real-time system for detecting, preventing, and responding to cyber threats. Instead of security teams working separately from IT teams, SecOps fosters collaboration, ensuring that security is embedded into every process, tool, and workflow.
Why Do We Need SecOps?

Think about the way cyber threats have evolved. Gone are the days when a simple antivirus program was enough to protect a company’s data. Today, cybercriminals use advanced tactics like ransomware, phishing, and supply chain attacks to infiltrate systems. Organizations need to move from a reactive to a proactive approach—this is where SecOps becomes essential.
Key Reasons We Need SecOps:
- Cyber Threats Are Growing Rapidly – Hackers are constantly developing new attack methods. Without a proper security strategy, organizations remain vulnerable.
- Security Breaches Can Be Devastating – Data breaches result in financial losses, reputation damage, legal consequences, and loss of customer trust.
- Compliance & Regulations – Industries such as healthcare, finance, and e-commerce must meet strict cybersecurity regulations (e.g., GDPR, HIPAA, PCI-DSS). Non-compliance can lead to heavy fines.
- IT Systems Are Becoming More Complex – Businesses now operate in hybrid environments (on-premises, cloud, and remote work). Managing security across these platforms requires a streamlined approach.
- Faster Incident Response Is Critical – A security breach can happen in seconds, and organizations need a quick response system to mitigate damage.
SecOps ensures that businesses don’t just react to cyberattacks but are prepared to prevent them before they occur.
What Are the Advantages of SecOps?
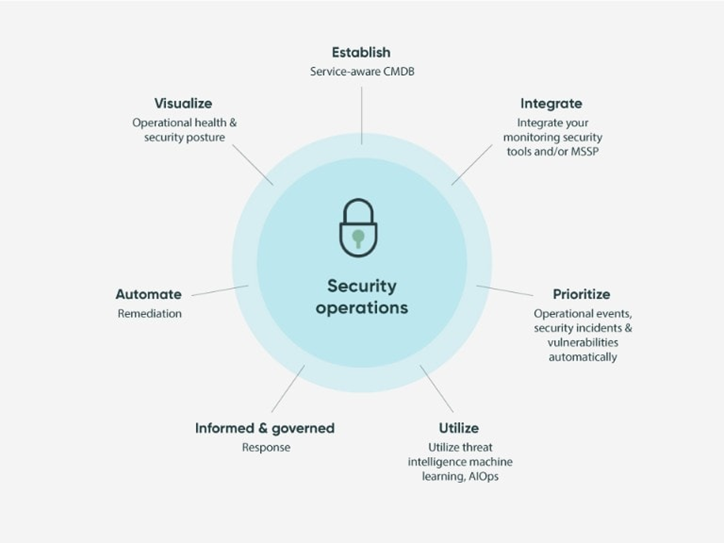
Adopting SecOps offers a wide range of benefits for businesses of all sizes. Here’s why organizations are making SecOps a priority:
1. Stronger Threat Detection & Faster Response
SecOps utilizes advanced security tools and real-time monitoring to identify suspicious activity as soon as it happens. Instead of detecting a breach days or weeks later, organizations can respond within minutes, reducing potential damage.
2. Enhanced Collaboration Between Teams
Traditionally, IT and security teams operate in silos, leading to miscommunication and slow responses to threats. SecOps brings them together, allowing seamless incident management and threat mitigation.
3. Cost Savings & Business Continuity
Cyberattacks can be expensive. The costs of downtime, legal fees, and data recovery can cripple a business. SecOps helps organizations prevent costly breaches and ensures smooth business operations.
4. Automation Reduces Human Errors
Many security incidents result from human mistakes—such as weak passwords or unpatched software. SecOps integrates automation tools that manage patch updates, threat detection, and compliance checks without relying on manual processes.
5. Compliance & Risk Management
Companies must follow strict regulations regarding data privacy and security. SecOps simplifies compliance auditing and ensures security policies align with industry standards.
6. Proactive Security Approach
Rather than reacting to attacks, SecOps prevents threats by continuously monitoring networks, identifying vulnerabilities, and addressing them before they can be exploited.
Key Features of SecOps
To understand how SecOps works, let’s break down some of its core components that help organizations stay secure:
1. Security Information & Event Management (SIEM)
SIEM platforms like Splunk, IBM QRadar, and Microsoft Sentinel collect and analyze security data from different sources (logs, network traffic, user activity) to identify potential threats.
2. Security Orchestration, Automation, and Response (SOAR)
SOAR tools automate security workflows, reducing response time to threats and minimizing manual intervention.
3. Threat Intelligence & Detection
Using AI-driven analytics, SecOps continuously scans for anomalous behavior and compares it with global threat databases to detect cyberattacks.
4. Endpoint Detection & Response (EDR)
This feature ensures that devices like laptops, desktops, and mobile phones remain secure against malware, ransomware, and unauthorized access.
5. Incident Response & Forensics
SecOps includes forensic tools that help organizations investigate breaches, identify how an attack happened, and strengthen security measures to prevent future incidents.
6. Vulnerability & Patch Management
One of the easiest ways for hackers to breach systems is by exploiting unpatched software vulnerabilities. SecOps ensures timely patch updates to prevent such security gaps.
Top 10 Use Cases of SecOps
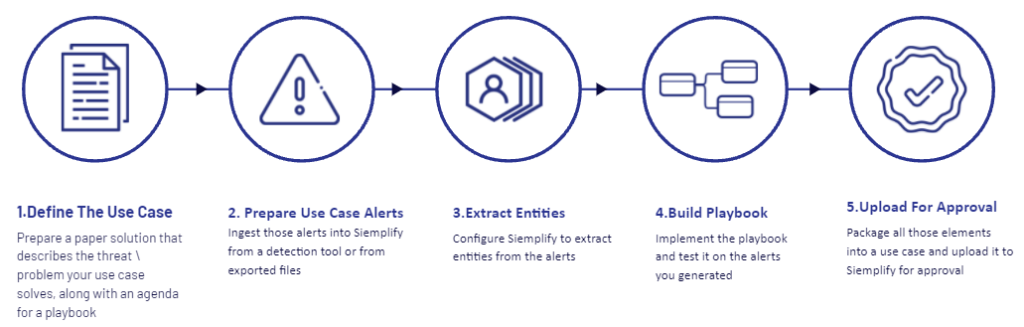
SecOps can be applied in various scenarios, making it one of the most versatile security strategies for businesses today. Here are some real-world applications:
- Early Threat Detection & Response – Quickly identify and mitigate security incidents before they escalate.
- Preventing Ransomware Attacks – Monitor suspicious behavior and stop ransomware before it encrypts files.
- Managing Insider Threats – Detect unauthorized employee access to sensitive data.
- Cloud Security Monitoring – Ensure that cloud services (AWS, Azure, Google Cloud) comply with security policies.
- Automated Incident Handling – Use SOAR to automate responses to security threats.
- Data Loss Prevention (DLP) – Prevent sensitive information (e.g., financial data, customer records) from being leaked.
- Zero Trust Security Model – Apply a zero-trust approach to limit access based on strict identity verification.
- Regulatory Compliance Audits – Continuously monitor security logs to prove compliance with industry regulations.
- Patch & Vulnerability Management – Keep software up-to-date to eliminate security weaknesses.
- Phishing Attack Mitigation – Detect and block email-based phishing scams.
How to Implement SecOps?
SecOps implementation requires a structured and strategic approach. Here’s a step-by-step guide to getting started:
Step 1: Define Security & IT Operations Goals
Clearly outline what you aim to achieve with SecOps—whether it’s threat prevention, compliance, or improving security response time.
Step 2: Build a Dedicated SecOps Team
Your SecOps team should include IT administrators, security analysts, DevOps engineers, and compliance officers who work together to secure the infrastructure.
Step 3: Deploy Security Tools (SIEM & SOAR)
Implement tools like Splunk, IBM QRadar, Palo Alto Cortex XSOAR for real-time security monitoring and automated response workflows.
Step 4: Automate Threat Detection & Response
Use AI-driven threat detection systems to analyze user behavior, network activity, and security logs for anomalies.
Step 5: Implement Zero Trust Security Policies
Ensure that every user and device must verify their identity before accessing critical systems.
Step 6: Perform Continuous Security Monitoring
Monitor logs, analyze security alerts, and track potential threats 24/7.
Step 7: Regular Security Audits & Compliance Checks
Conduct periodic security assessments to detect gaps and vulnerabilities in the IT environment.
Step 8: Train Employees on Cybersecurity Best Practices
Security is everyone’s responsibility—educate employees on phishing attacks, password management, and safe browsing habits.