Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
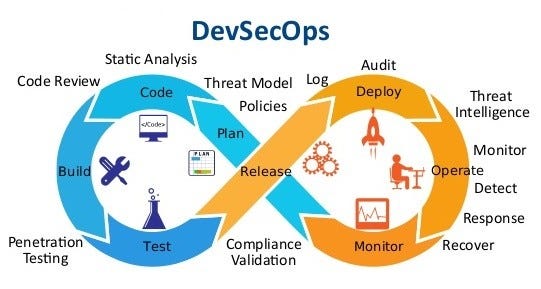
Here is a list of 100 tools used in DevSecOps, along with a brief description of each:
OWASP ZAP:
A widely-used open source web application security scanner.
Burp Suite:
A popular suite of tools for web application security testing, including a web proxy, scanner, and vulnerability management tools.
Kali Linux:
A Linux-based penetration testing distribution, used for a wide range of security testing activities.
Metasploit:
A penetration testing framework used for developing and executing exploits against various targets.
Nmap:
A network scanner used for identifying hosts and services on a network.
Wireshark:
A network protocol analyzer used for troubleshooting network issues and analyzing network traffic.
Snort:
A popular intrusion detection system (IDS) used to detect and prevent network attacks.
OSSEC:
An open source host-based intrusion detection system (HIDS) that can be used to monitor and analyze system logs and events.
Splunk:
A log management and analysis tool used to monitor and analyze logs from various sources.
Logstash:
A log management tool used to collect, parse, and analyze log data from various sources.
Elasticsearch:
A distributed search and analytics engine used to store and search large amounts of data.
Grafana:
A data visualization and monitoring tool used to create dashboards and visualizations from various data sources.
Prometheus:
A monitoring and alerting tool used to collect and store metrics from various sources.
Nagios:
A widely-used monitoring tool used to monitor hosts and services on a network.
Icinga:
A popular monitoring tool used for monitoring hosts and services on a network.
Ansible:
A popular configuration management tool used for automating IT infrastructure tasks.
Puppet:
A popular configuration management tool used for automating IT infrastructure tasks.
Chef:
A popular configuration management tool used for automating IT infrastructure tasks.
SaltStack:
A popular configuration management tool used for automating IT infrastructure tasks.
Terraform:
A popular infrastructure as code tool used for automating infrastructure provisioning and management.
Packer:
A tool used for creating machine images for various platforms.
Docker:
A containerization platform used for creating and managing containers.
Kubernetes:
A container orchestration platform used for managing containerized applications.
AWS:
Amazon Web Services, a popular cloud computing platform used for hosting and managing applications and infrastructure.
Azure:
Microsoft Azure, a popular cloud computing platform used for hosting and managing applications and infrastructure.
Google Cloud:
Google Cloud Platform, a popular cloud computing platform used for hosting and managing applications and infrastructure.
Git:
A popular version control system used for managing code changes and collaboration.
GitLab:
A popular web-based Git repository manager used for managing code changes and collaboration.
GitHub:
A popular web-based Git repository hosting service used for managing code changes and collaboration.
Jenkins:
A popular open source automation server used for continuous integration and delivery.
Travis CI:
A cloud-based continuous integration and delivery platform used for automating software development workflows.
CircleCI:
A cloud-based continuous integration and delivery platform used for automating software development workflows.
Selenium:
A popular web application testing framework used for automating browser-based tests.
Cucumber:
A popular BDD (behavior-driven development) testing framework used for automating tests and specifications.
JMeter:
A popular load testing tool used for testing web applications and services.
Postman:
A popular tool used for testing and documenting APIs.
SonarQube:
A popular code quality and security analysis tool used to identify and resolve code issues.
Twistlock:
A container security platform that enables vulnerability management, compliance enforcement, and runtime defense.
GitLab:
An end-to-end DevOps platform that includes source code management, continuous integration and delivery, and security testing.
ThreadFix:
A vulnerability management platform that consolidates and triages application vulnerabilities across disparate systems.
Anchore:
A container security platform that provides vulnerability management, policy-based compliance, and runtime security monitoring.
Aqua Security:
A platform for securing cloud-native applications that includes vulnerability management, compliance enforcement, and runtime protection.
Veracode:
A cloud-based application security testing platform that includes static, dynamic, and software composition analysis.
Sysdig:
A platform for securing containerized applications that includes vulnerability management, compliance enforcement, and runtime defense.
AppScan:
An application security testing tool that includes static, dynamic, and software composition analysis.
Sqreen:
A platform for securing web applications that includes runtime protection, application monitoring, and vulnerability scanning.
Checkmarx:
A platform for securing software development that includes static and dynamic application security testing, as well as software composition analysis.
Bandit:
A Python code analysis tool that detects security vulnerabilities in Python applications.
Snort:
An open-source intrusion detection and prevention system that analyzes network traffic for malicious activity.
Tripwire:
A tool that monitors changes to system files and alerts administrators to any unauthorized modifications.
OSSEC:
An open-source host-based intrusion detection system that monitors file changes, log files, and other system events for signs of compromise.
Apache Fortress:
An open-source access management system that provides role-based access control, password policies, and auditing capabilities.
CredDefense:
A tool that detects and prevents attempts to steal sensitive data, such as credentials, from memory.
BeEF:
The Browser Exploitation Framework is a tool for testing web browsers for vulnerabilities, such as cross-site scripting and CSRF attacks.
RIPS:
A PHP security analysis tool that detects vulnerabilities such as SQL injection, cross-site scripting, and remote file inclusion.
FuzzDB:
A collection of payloads and attack patterns for testing web application security.
YARA:
A tool for creating custom rules to detect malware, suspicious files, and other indicators of compromise.
Vuls:
A vulnerability scanner for Linux and Unix systems that includes configuration checking, CVE scanning, and open port scanning.
InSpec:
A tool for automating security and compliance testing that includes a domain-specific language for defining tests.
Clair:
An open-source container security analyzer that provides vulnerability scanning and monitoring of container images.
Wazuh:
An open-source security monitoring platform that includes intrusion detection, log analysis, and file integrity monitoring.
Google Lighthouse:
A tool for auditing the performance and accessibility of web applications.
ZAP:
The Zed Attack Proxy is a tool for testing web applications for vulnerabilities, including OWASP Top Ten issues.
Nessus:
A vulnerability scanner that includes network scanning, configuration auditing, and compliance checking.
Lynis:
A security auditing tool for Linux and Unix systems that checks for vulnerabilities, configuration issues, and system hardening.
WPScan:
A tool for testing the security of WordPress installations, including vulnerability scanning and password cracking.
OSQuery:
A tool for querying operating system data using SQL, enabling security monitoring and threat detection.
HashiCorp Vault:
A tool for managing secrets and sensitive data, including authentication and authorization mechanisms.
OPA:
The Open Policy Agent is a policy engine for enforcing security and compliance policies across different services and systems


Leave a Reply