Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
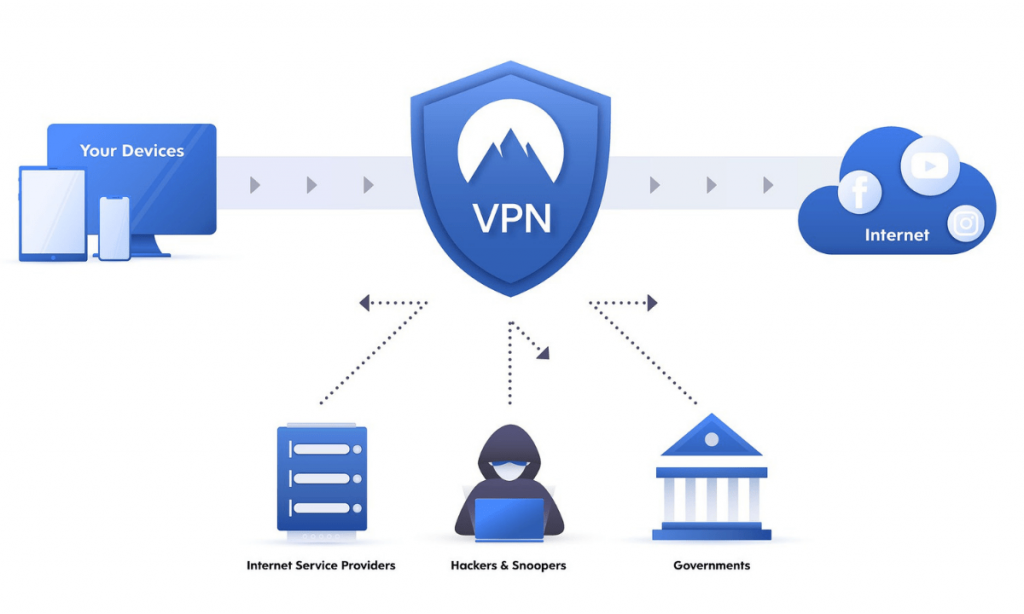
The virtual private network is known as a VPN. Technology known as a virtual private network (VPN) establishes a secure, encrypted link over a less secure network, such the Internet. Using a public network like the Internet, a virtual private network can be used to expand a private network. All that the term implies is that it is a virtual “private network,” meaning that a person may join a local network when they are at a distance. To provide a secure connection, it uses tunneling techniques.
How Virtual Private Networks (VPNs) Works?
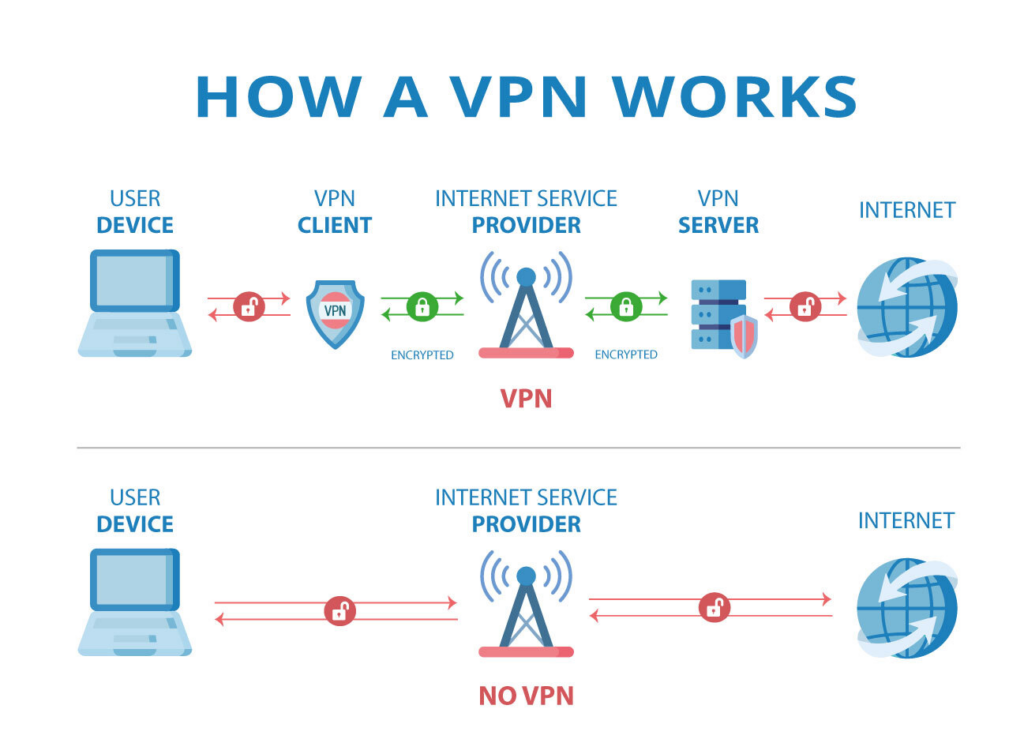
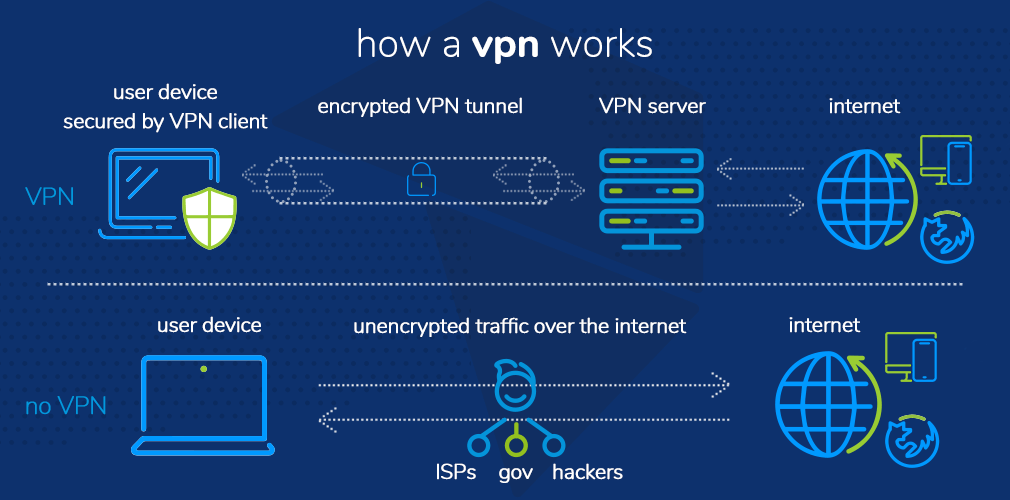
With a VPN, your IP address is hidden by having the network route it via a distant server that is managed by a VPN host and has been carefully configured. This implies that your data originates from the VPN server when you browse the internet using one. This implies that the websites you visit and the information you transmit and receive online are hidden from your Internet Service Provider (ISP) and other third parties. Using a VPN is similar to using a filter to convert all of your data to “gibberish”. Your data wouldn’t be worth anything even if it were stolen.
Encryption:
Your data is encrypted before it leaves your device and goes over the internet when you connect to a VPN. By using encryption, you can make sure that even if someone manages to intercept the data, they won’t be able to decrypt it or use it for their own purposes.
Tunneling:
VPNs establish a secure connection using a procedure known as tunneling. To do this, the data must be encapsulated in a different set of data packets. The inner data is shielded from the outside as it passes across the internet by this layer.
Authentication:
In order to guarantee that only authorized users may access the network, VPNs frequently need authentication. Passwords, usernames, and more secure techniques like certificates or two-factor authentication may be used in this.
Privacy and Anonymity:
VPNs may help improve anonymity and privacy by hiding your IP address. An additional degree of anonymity is added when you connect to a VPN server since it makes your internet traffic appear to be coming from the server’s location rather than your own.
What are the benefits of a VPN connection?
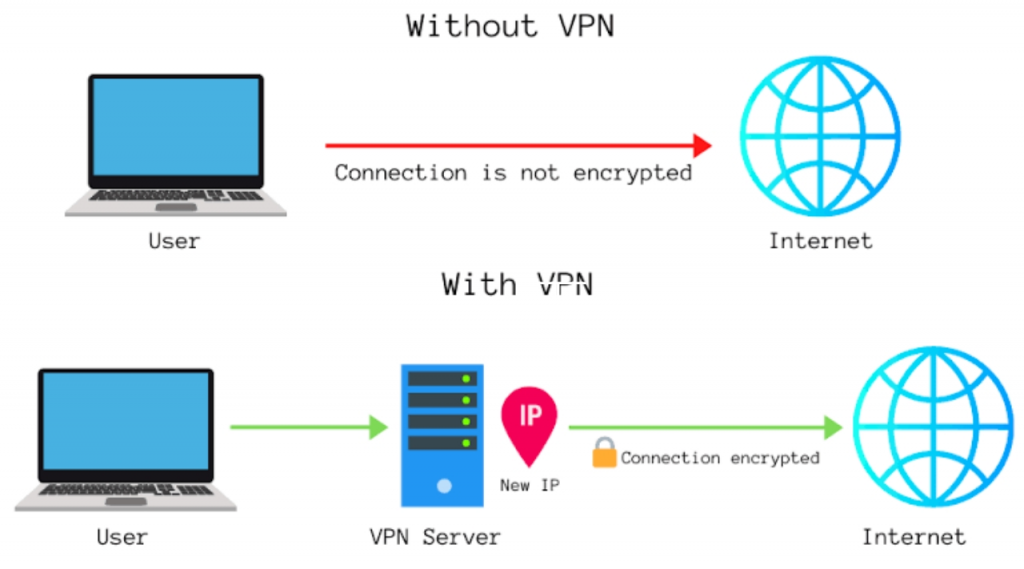
Your internet data transmission is concealed via a VPN connection, shielding it from prying eyes. Anyone with network access who wants to read unencrypted data can do so. Hackers and online criminals are unable to decode this data when using a VPN.
Secure encryption: An encryption key is required in order to read the data. Without one, a brute force assault on a computer would take millions of years to decode the code. Your internet activity is concealed, even while using public networks, with the use of a VPN.
Disguising your whereabouts : VPN servers function as your online proxies in essence. Your precise location cannot be ascertained since the demographic location data originates from a server located in a different nation. Furthermore, the majority of VPN providers don’t keep activity logs. Conversely, some service providers log your activity but do not share this data with outside parties. This implies that whatever information about your user behavior that may exist now is kept secret forever.
Access to regional content: Not all websites provide universal accessibility for their content. Content on websites and services is frequently restricted to users located in specific regions of the globe. Standard connections use national local servers to pinpoint your location. This implies that you are unable to view stuff from abroad from home and vice versa when traveling. You may “change” your location by using VPN location spoofing to move to a server in a different nation.
Secure data transfer: You might need to access critical files on your company’s network if you operate remotely. This type of data has to be transferred over a secure connection for security reasons. Usually, you need a VPN connection in order to access the network. VPN services lower the danger of data leaking by connecting to private servers and use encryption techniques.
Why should you use a VPN connection?
When you connect to the internet, your connection is typically set up by your ISP. It uses your IP address to monitor you. Your ISP’s servers handle the routing of your network traffic, and they have the ability to record and show anything you do online.
Even if your ISP seems reliable, it could provide advertising, the government, the police, and/or other third parties access to your surfing data. Cybercriminals may also launch attacks against ISPs: Your sensitive information may be jeopardized if they are compromised.
If you often connect to public Wi-Fi networks, this is quite crucial. You never know who may be keeping an eye on your online activities or what kind of information, including passwords, credit card numbers, personal information, or even your complete identity, they might take.
What are VPNs used for?
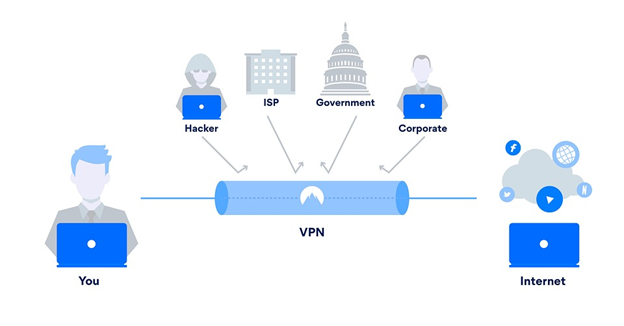
VPNs are utilized for virtual privacy by businesses as well as regular internet users. VPNs are a useful tool for organizations to ensure that external users accessing their data center are permitted and utilizing encrypted routes. VPNs may also be used to establish a connection to a database from a separate location that belongs to the same enterprise.
VPNs can also be used to access software hosted on proprietary networks for gig economy freelancers, distant workers, and business travelers. The user must be permitted to use the virtual private network and supply one or more authentication factors in order to access a restricted resource over a VPN. Passwords, security tokens, and biometric information might be among them.
An attacker may be able to get information about a web user, such as their IP address or browsing history. Users can feel secure using a VPN if privacy is an issue. Most users value encryption, privacy, and the ability to bypass content that is prohibited in certain regions while using a VPN.
For journalists, for example, being able to bypass banned information from another nation may be quite helpful. Journalists might use a VPN to appear as though they are inside a nation that is likely to prohibit online material from outside sources.
What are the types of VPNs are there?
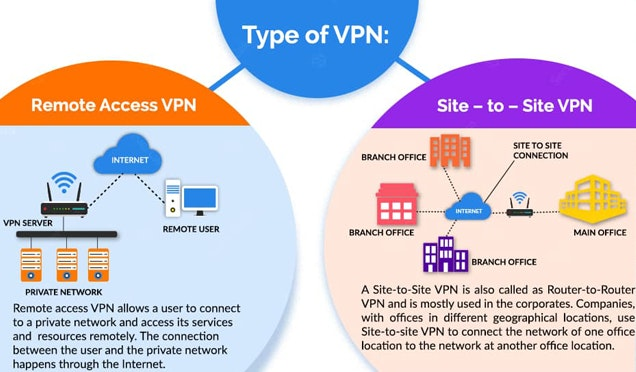
Although there are numerous varieties of VPNs, you should at least be aware of the following three:
SSL VPN
Not every person in an organization has access to a laptop that they can use to work from home. Many businesses had the issue of not having enough equipment for their staff during the 2020 spring Corona crisis. Using a private device (PC, laptop, tablet, or mobile phone) is frequently used in these situations. Businesses typically rely on an SSL-VPN solution in this situation, which is typically deployed through a matching hardware box.
To access the company’s login website, a browser that supports HTML-5 is often required. There are browsers that support HTML-5 for almost every operating system. Using a username and password protects access.
Site-to-site VPN
From site to site In essence, a VPN is a private network that is used to conceal private intranets and enable users to access each other’s resources.
If your business has several sites, each having a local area network (LAN) linked to the wide area network (WAN), a site-to-site VPN might be helpful. If you have two distinct intranets and wish to transfer data between them without requiring users from one intranet to actively visit the other, site-to-site VPNs can be helpful.
Site-to-site VPNs are generally utilized in large enterprises. They lack the flexibility of SSL VPNs and are difficult to set up. Nonetheless, they are the best means of guaranteeing communication both inside and between sizable departments.
Client-to-Server VPN
You may think of connecting through a VPN client as if you were using an extension cord to connect your home computer to the business. Workers can use the secure connection to dial into the corporate network from their home office and pretend to be in the office. On the PC, a VPN client has to be installed and set up first.
This entails the user connecting directly to the internet via his or her VPN provider rather than through their own ISP. In essence, this cuts down on the VPN’s tunnel leg. The VPN may automatically encrypt the data before it is made available to the user, saving them from having to utilize it to construct an encryption tunnel to hide their current internet connection.
How do I install a VPN on my computer?
Understanding the various implementation techniques is essential when deploying a VPN.
- VPN client: Installation of software is required for standalone VPN clients. The configuration of this program complies with the endpoint’s specifications. The endpoint establishes the encryption tunnel by connecting to the other endpoint and executing the VPN connection during VPN setup. This stage typically calls for the installation of the necessary certificate or the entering of a password that the firm has supplied. The firewall is able to identify that this is an authorized connection by utilizing a password or certificate. The employee then uses credentials that they are familiar with to verify their identity.
- Browser extensions: VPN extensions are compatible with the majority of web browsers, including Firefox and Google Chrome. Opera is one of the browsers that has its own built-in VPN addons. Users may instantly switch and setup their VPN while browsing the internet with the help of extensions. Nevertheless, the VPN connection is limited to sharing data through this browser. The VPN cannot encrypt usage of other browsers or other internet activities (like playing online games). Although browser extensions are not as feature-rich as VPN software, they could be a good choice for infrequent internet users who want an additional degree of protection. They have, nonetheless, shown to be more vulnerable to breaches. Additionally, users are cautioned to use a reliable extension because data harvesters can try to utilize phony VPN extensions. The gathering of personal information, such as that which marketing strategists conduct to build an individual profile of you, is known as data harvesting. After then, advertising information is customized just for you.
- Router VPN: It could be simpler to install a VPN directly on the router rather than one on each device if several devices are using the same internet connection. If you want to secure internet-connected devices that are difficult to configure, such smart TVs, a router VPN is quite helpful. They may also assist you in using your home entertainment devices to get material that is regionally prohibited. Installing a router VPN is simple, it always offers security and privacy, and it keeps your network safe from hacking attempts made by unauthorized devices. However, if your router lacks a user interface of its own, it could be more challenging to operate. This may result in the blocking of incoming connections.
- Company VPN: A corporate VPN is a unique solution that has to be set up and maintained by a technical support specialist. Usually, the IT department of the firm creates the VPN for you. The VPN does not provide you any administrative control, and your business logs all of your activity and data transfers. By doing this, the business can reduce the possibility of data leaks. The primary benefit of a corporate VPN is that it allows employees—even those who work remotely—to connect securely to the intranet and server of the business.
Conclusion
An encrypted link is created between you and the internet via a VPN connection. Your whole data traffic is routed over an encrypted virtual tunnel using the VPN. When you utilize the internet, this masks your IP address, rendering its location undetectable to outside observers. Moreover, a VPN connection is safe from outside threats. This is due to the fact that nobody else can access the data in the encrypted tunnel as they do not possess the key, only you. With a VPN, you may access information that is geographically prohibited from any location in the globe. There are some streaming services that aren’t accessible everywhere. With the VPN, you can still access them. Kaspersky offers VPN services for Macintosh and Windows computers.




Thanks for sharing it has pretty good content regarding VPN connections. i m imperesed with this
best views on virtual private network…