Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
What is Single Sign-On (SSO)?
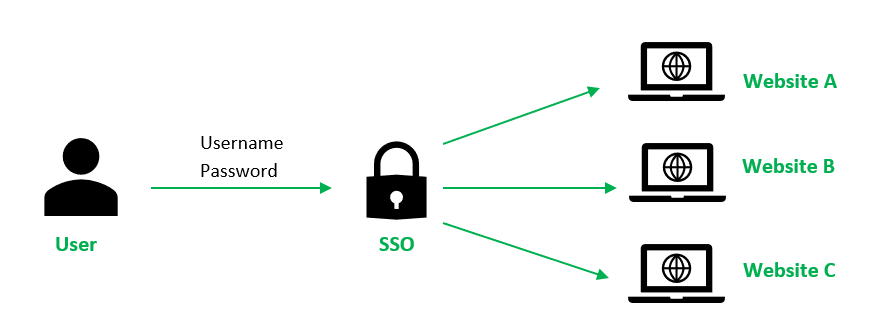
Single Sign-On (SSO) is an authentication method designed to enhance both security and user experience by allowing users to access multiple applications, systems, or websites with a single set of credentials. Instead of requiring users to manage separate usernames and passwords for each application, SSO creates a seamless experience where one login session grants access to all authorized systems.
SSO works by establishing trust between an identity provider (IdP) and multiple service providers (SP). When a user logs in, the identity provider authenticates the credentials and generates a secure token. This token is used to validate the user’s identity across connected applications, eliminating the need for repeated logins.
Why Do We Need SSO?
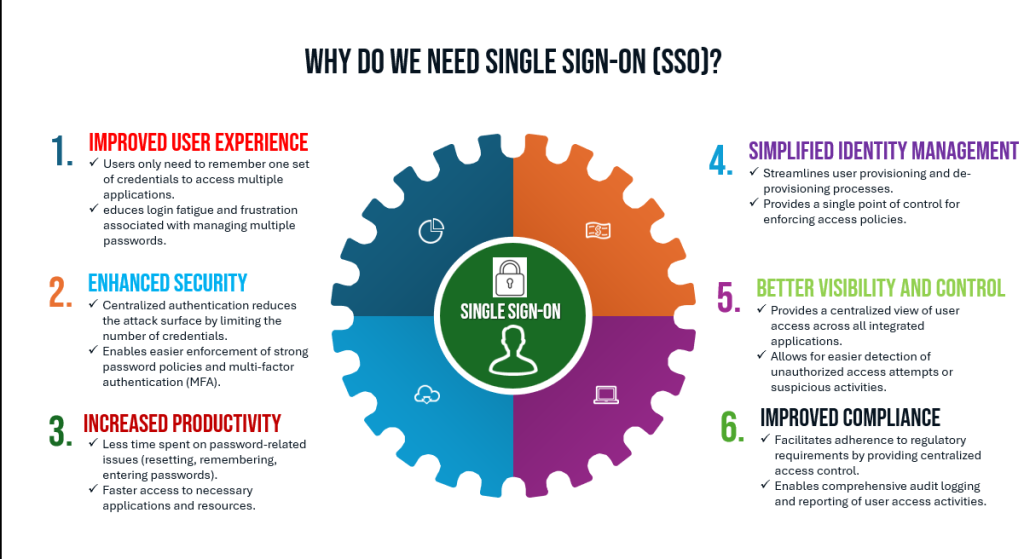
Organizations and users face numerous challenges with traditional authentication methods. Here’s why SSO is essential:
- Enhanced User Experience: Users no longer need to remember or repeatedly enter multiple credentials for different platforms. This convenience reduces frustration and enhances satisfaction.
- Improved Security: SSO centralizes authentication, enabling the implementation of robust security policies like strong passwords, multi-factor authentication (MFA), and adaptive authentication. It reduces the risk of password-related security breaches.
- Operational Efficiency: IT departments spend significant time and resources on password resets and account recovery. SSO minimizes these tasks, leading to cost savings and increased efficiency.
- Regulatory Compliance: Industries with stringent regulatory requirements, such as healthcare and finance, benefit from SSO’s logging and monitoring capabilities, which support compliance with GDPR, HIPAA, and other standards.
- Scalability for Growing Organizations: As businesses expand and adopt more applications, SSO ensures that managing user access remains efficient and scalable.
What are the Advantages of SSO?

The advantages of SSO go beyond just convenience. Some of the key benefits include:
- Streamlined Access Across Applications: Users can seamlessly navigate between multiple connected platforms without repeated logins.
- Enhanced Productivity: Employees and users save time by avoiding the need to log in repeatedly, allowing them to focus on their tasks.
- Reduced IT Costs: By decreasing password-related support tickets, SSO reduces the workload on IT helpdesks.
- Strengthened Security: By centralizing authentication, SSO reduces weak password practices and mitigates risks such as phishing and credential theft.
- Simplified User Management: Administrators can manage user access, roles, and permissions across all applications from a single dashboard.
- Flexible Integration: SSO integrates seamlessly with cloud-based, on-premise, and hybrid systems, making it suitable for diverse IT environments.
- Minimized Risk of Account Lockouts: SSO’s centralized approach reduces instances of forgotten credentials and account lockouts.
What are the Features of SSO?
SSO tools offer various features that make them essential for modern organizations:
- Centralized Authentication: A single access point for multiple applications and systems.
- Secure Token Exchange: Uses industry-standard protocols like SAML (Security Assertion Markup Language), OAuth, or OpenID Connect to ensure secure communication between identity providers and service providers.
- Integration with Directory Services: Compatibility with popular directories like LDAP, Active Directory (AD), and cloud-based identity services.
- Multi-Factor Authentication (MFA): Adds an extra layer of security to the login process.
- Role-Based Access Control (RBAC): Ensures users only access systems and data relevant to their roles.
- Session Management: Facilitates continuous access while maintaining security controls during active sessions.
- Customizable Branding: Allows organizations to tailor the login interface to reflect their branding.
- Robust Audit Trails: Provides detailed logs of user activity, aiding in compliance and security monitoring.
Top 10 Use Cases of SSO
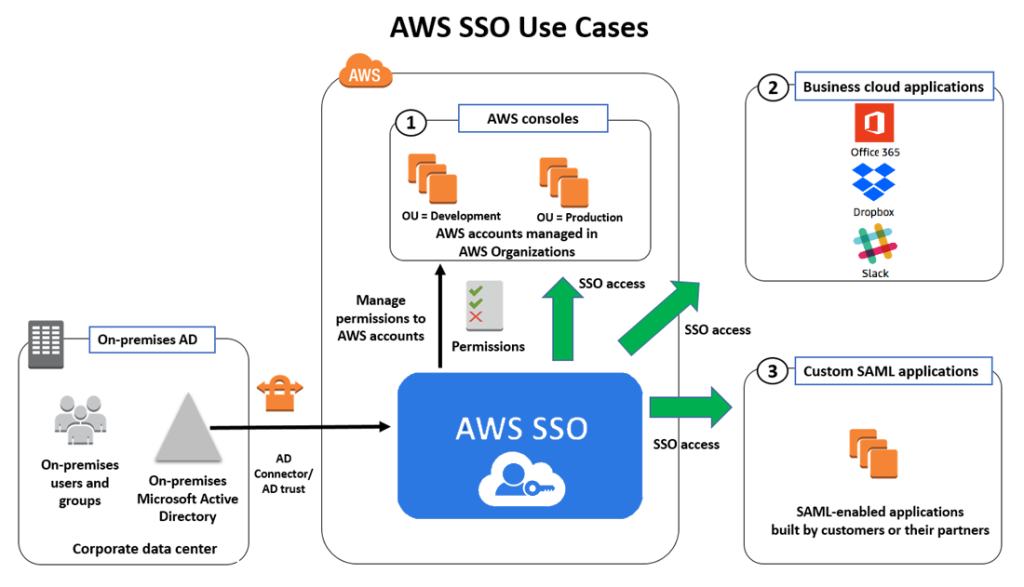
SSO can be implemented across various industries and scenarios. Here are the top 10 use cases:
- Enterprise Applications Access: Employees gain seamless access to productivity tools like Microsoft 365, Salesforce, and Slack.
- Customer Portals: Enhances the customer experience by providing unified access to multiple services within an ecosystem.
- Education Systems: Enables students and educators to log in once to access learning platforms, email, and library systems.
- Healthcare Systems: Ensures secure, efficient access to electronic health records (EHRs), telemedicine platforms, and billing systems.
- eCommerce Platforms: Simplifies the shopping experience for customers using multiple online storefronts.
- Cloud-Based Solutions: Centralizes access to cloud platforms such as AWS, Google Workspace, and Dropbox.
- Partner and Vendor Portals: Provides third-party stakeholders with secure and convenient access to collaboration tools and resources.
- Government Services: Simplifies access to multiple e-government platforms for citizens and government employees.
- Remote Work Enablement: Secures access to collaboration tools, virtual desktops, and VPNs for distributed teams.
- Financial Services: Improves the user experience and security for banking, trading, and investment platforms.
How to Implement SSO
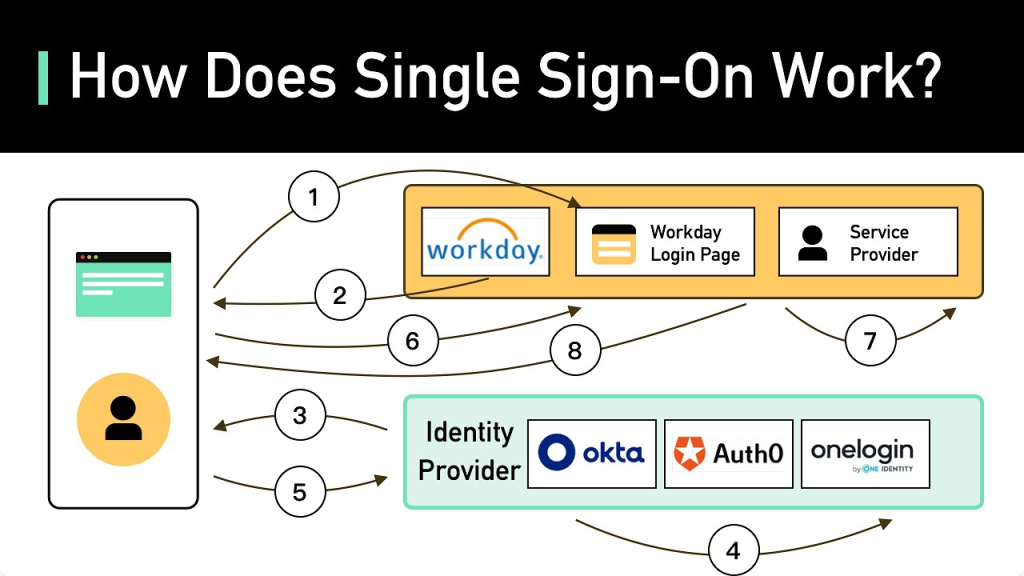
Implementing SSO involves several key steps to ensure a seamless and secure experience:
- Assess Requirements: Identify the applications, systems, and platforms that need SSO integration. Evaluate your organization’s security, compliance, and scalability needs.
- Choose the Right SSO Tool: Research and select an SSO solution that aligns with your organization’s requirements. Popular tools include Okta, Ping Identity, Microsoft Azure AD, OneLogin, and Auth0.
- Integrate with Directory Services: Connect the SSO tool to your existing directory (e.g., Active Directory or LDAP) to manage user identities effectively.
- Enable Secure Authentication Protocols: Use industry-standard protocols like SAML, OAuth, or OpenID Connect to ensure secure communication between the identity provider and service providers.
- Configure Applications: Set up each application to work with the SSO system by configuring service provider settings and ensuring proper token handling.
- Implement Multi-Factor Authentication (MFA): Strengthen authentication security by requiring additional verification steps.
- Test the Integration: Conduct thorough testing to verify that users can seamlessly and securely access all integrated systems.
- Train Users: Provide training and documentation to employees and stakeholders, ensuring they understand how to use the SSO system.
- Monitor and Maintain: Regularly review access logs, address security vulnerabilities, and update configurations to keep the system secure and efficient.
By implementing SSO, organizations can achieve a harmonious balance between user convenience, robust security, and efficient operations. Whether you are enhancing employee productivity, securing customer portals, or complying with regulatory standards, SSO offers a scalable solution tailored to modern authentication challenges.

Leave a Reply