Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
What is Qualys
Qualys is a cloud security company that provides a variety of security and compliance solutions to businesses and organizations. The company’s flagship product is the Qualys Cloud Platform, which offers a suite of security and compliance tools designed to help businesses detect security vulnerabilities, ensure compliance with various standards and regulations, and protect their IT assets and data.
The Qualys platform includes features for vulnerability management, continuous monitoring, threat protection, web application scanning, and security assessments. The system operates on a software-as-a-service (SaaS) model, meaning that it is accessible over the internet without the need for on-premise hardware, making it scalable and easy to deploy for organizations of all sizes.
Overall, Qualys is recognized for its ability to provide comprehensive security solutions that help companies identify and mitigate risks in their network environments, applications, and cloud services.
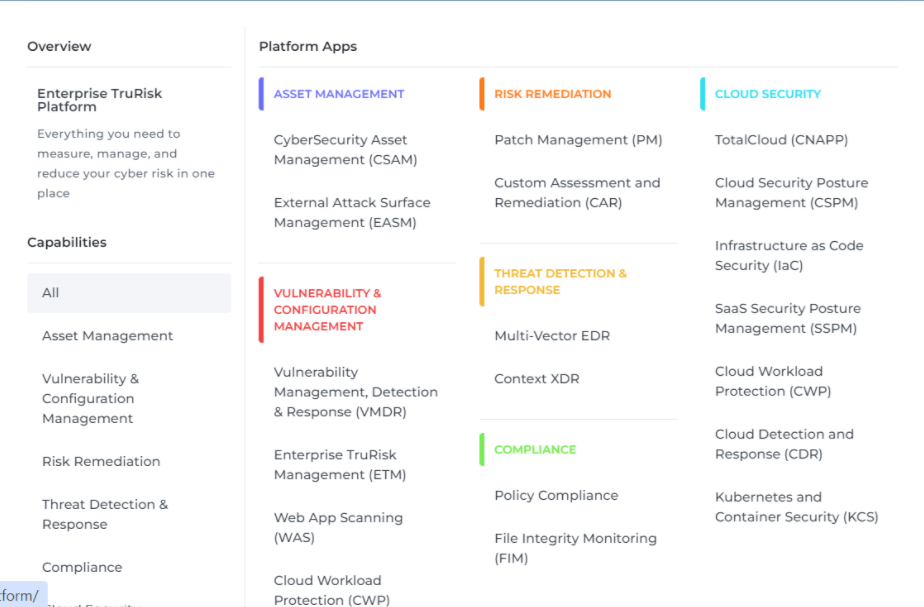
List of products of Qualys

Qualys offers a range of security and compliance products within its cloud platform. As of my last update, here’s a list of some key products and services provided by Qualys:
- Vulnerability Management (VM): Scans and identifies vulnerabilities in networks, servers, endpoints, and other IT assets.
- Continuous Monitoring (CM): Provides real-time monitoring of networks and devices to quickly detect threats and changes in network configurations.
- Web Application Scanning (WAS): Detects vulnerabilities in web applications and provides automated crawling and testing for common security issues.
- Web Application Firewall (WAF): Offers protection for web applications from attacks and vulnerabilities, with customizable security rules.
- Policy Compliance (PC): Helps ensure systems are compliant with internal policies and external regulations by continuously auditing configurations against compliance requirements.
- File Integrity Monitoring (FIM): Detects and alerts on unauthorized changes to files and directories.
- Patch Management: Automates the patching process for vulnerabilities across devices and operating systems.
- Security Assessment Questionnaire (SAQ): Simplifies risk assessment and compliance processes with customizable questionnaires and scalable campaigns.
- Threat Protection: Identifies active threats by correlating real-time threat data against vulnerability and asset information.
- Asset Inventory (AI): Provides real-time visibility of all IT assets, wherever they are located (on-premise, endpoints, clouds, containers, mobile, OT and IoT).
- Container Security: Analyzes container images and running containers for vulnerabilities, hardening issues, and runtime threats.
- Certificate Inventory: Scans and catalogs all SSL/TLS certificates in the network to manage their expiration and compliance.
How Qualys Vulnerability Management, Detection and Response (VMDR) Works?
The architecture of Qualys Vulnerability Management, Detection, and Response (VMDR) is designed to provide a scalable, cloud-based solution for continuous asset discovery, security assessments, vulnerability management, and compliance monitoring. Here’s a breakdown of its architecture:
1. Cloud Platform
- Centralized Management: The core of VMDR is the Qualys Cloud Platform, which manages all data and operations. This platform is responsible for processing and storing vast amounts of vulnerability and configuration data securely.
- High Scalability: As a cloud-based service, VMDR can scale to handle assets and data from small to very large enterprises without the need for on-premise infrastructure adjustments.
2. Qualys Cloud Agents
- Continuous Monitoring and Scanning: These lightweight agents are installed on the endpoints and other IT assets. They continuously collect and send data back to the Qualys Cloud Platform regarding the asset’s configuration, running services, installed software, and potential vulnerabilities.
- Real-time Data: Agents provide real-time data which helps in immediate identification and response to new vulnerabilities and threats.
3. Scanner Appliances
- Internal and External Scanning: Qualys offers physical and virtual scanner appliances that can be deployed within the network for internal scans or positioned externally for perimeter scanning.
- Automated Scans: These appliances perform scheduled and triggered vulnerability scans to identify risks across the network without the need for agent installation on every asset.
4. Network Discovery
- Passive Scanning: VMDR includes passive scanning capabilities that help in identifying devices that are connected to the network without sending active probing traffic, thereby reducing network load and avoiding disruptions.
5. Data Analysis and Threat Intelligence
- Global Threat Data: Qualys integrates global threat intelligence to enhance the vulnerability data with information about new vulnerabilities, existing exploits, and active threats.
- Analytics and Prioritization: The platform analyzes the data collected to identify critical vulnerabilities based on the threat landscape, asset criticality, and exploitability.
6. Response and Remediation
- Automated Workflows: VMDR can automate response workflows such as patch deployment or configuration changes based on the policies set by the organization.
- Integration Capabilities: The platform easily integrates with other IT security and management tools via APIs, allowing for streamlined remediation processes and enhanced incident response.
7. Reporting and Compliance
- Dashboards: Customizable dashboards provide insights into the organization’s overall security posture, highlighting areas of concern and tracking remediation progress.
- Regulatory Compliance: VMDR supports compliance reporting for various standards and regulations, ensuring that organizations meet necessary security compliance requirements.
How Qualys Container Security Works?
Qualys Container Security is a solution specifically designed to provide security for containerized applications. It integrates with the broader Qualys Cloud Platform to deliver comprehensive visibility and security across container environments. This includes everything from container images to container registries and the containers deployed in production. Here’s how Qualys Container Security works, especially focusing on how it scans container images:
1. Integration with Container Environments
- Compatibility: Qualys Container Security integrates with various container orchestration tools such as Kubernetes, as well as container registries like Docker Hub, Amazon ECR, and Google Container Registry. This allows it to seamlessly monitor and scan containers throughout their lifecycle.
- Automated Discovery: The system automatically discovers container images and registries within the environment, providing a complete inventory without manual intervention.
2. Scanning Container Images
- Continuous Scanning: Qualys performs continuous scanning of container images in registries, during build processes, and while they are running in production environments. This ensures that vulnerabilities are detected at every stage of the container lifecycle.
- Vulnerability Assessment: The scanning process involves examining container images for known vulnerabilities in the operating system layers, application dependencies, and binaries. It uses the extensive Qualys vulnerability knowledge base, which is regularly updated with the latest vulnerability signatures.
- Static and Dynamic Analysis: The scans include both static analysis (examining the contents of the container image without running it) and dynamic analysis (analyzing running containers to identify runtime vulnerabilities and misconfigurations).
- Drift Detection: For containers running in production, Qualys can detect changes or ‘drift’ from the original compliant state, identifying unauthorized or unexpected modifications that could introduce security risks.
3. Comprehensive Reporting
- Vulnerability Reports: After scanning, Qualys provides detailed vulnerability reports that include information on detected vulnerabilities, their severity, potential impacts, and recommended fixes or mitigation strategies.
- Compliance Checks: It also checks compliance with security best practices and regulatory standards, offering guidelines for securing container deployments according to established policies.
4. Integration and Automation
- API Access: Qualys Container Security offers API integration to automate security tasks and integrate with CI/CD pipelines, enhancing DevOps workflows and enabling a “shift-left” approach where security is integrated early in the development process.
- Alerts and Notifications: The platform can generate alerts and notifications for new vulnerabilities, compliance failures, or any configuration changes, facilitating rapid response to potential threats.
5. Security Policies and Configurations
- Policy Enforcement: Administrators can define security policies that specify acceptable risk levels and compliance requirements. Qualys will enforce these policies during the scanning and monitoring of containers.



