Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
Netskope is a cybersecurity company that focuses on cloud security. It provides a platform designed to secure data and protect against threats across various cloud services, apps, and web traffic.
Netskope’s platform is known for its ability to provide visibility and control over cloud usage, enforcing security policies, and ensuring compliance. It offers solutions for data loss prevention (DLP), cloud access security brokers (CASB), secure web gateways (SWG), and zero-trust network access (ZTNA). The platform helps organizations manage the risks associated with cloud adoption, ensuring that their data is secure no matter where it is accessed from or where it resides.
Netskope is particularly popular among enterprises that have adopted a hybrid or multi-cloud environment and need a comprehensive security solution that extends beyond traditional network perimeters.
List of Products of netskope
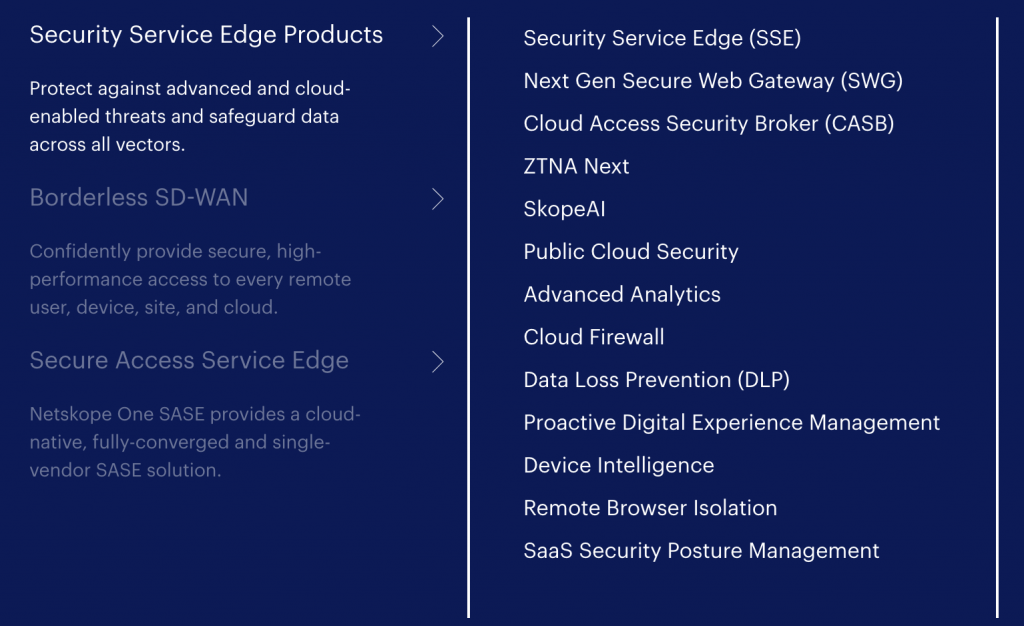

Netskope offers a range of products designed to provide comprehensive cloud security. Here’s a list of some key products and solutions offered by Netskope:
1. Netskope Cloud Access Security Broker (CASB)
- Provides visibility and control over cloud applications.
- Enforces security policies to protect sensitive data in the cloud.
- Helps in compliance with regulations and standards.
2. Netskope Secure Web Gateway (SWG)
- Protects users from web-based threats.
- Controls web traffic to prevent data loss and ensure compliance.
- Includes real-time threat protection and URL filtering.
3. Netskope Next Gen Secure Access Service Edge (SASE)
- Combines networking and security functions in a unified cloud-native service.
- Provides secure access to cloud applications, data, and the internet.
- Includes integrated CASB, SWG, and zero-trust network access (ZTNA).
4. Netskope Private Access (ZTNA)
- Enables secure access to private applications and data, whether hosted on-premises or in the cloud.
- Operates on a zero-trust model, ensuring that only authorized users can access specific resources.
5. Netskope Cloud Security Platform
- A unified platform offering visibility and protection across cloud apps, data, and users.
- Combines CASB, SWG, and DLP capabilities.
- Designed for securing both managed and unmanaged cloud services.
6. Netskope Data Loss Prevention (DLP)
- Protects sensitive data from being leaked or compromised.
- Provides real-time DLP capabilities across cloud, web, and email.
- Supports compliance with data protection regulations.
7. Netskope Threat Protection
- Offers advanced threat detection and response capabilities.
- Protects against malware, ransomware, and other advanced threats in the cloud.
- Integrates with other security solutions for comprehensive protection.
8. Netskope Advanced Analytics
- Provides deep insights and analytics on cloud usage and security events.
- Helps organizations understand risks, optimize security policies, and ensure compliance.
- Features customizable dashboards and reports.
9. Netskope Remote Browser Isolation (RBI)
- Isolates web browsing sessions to prevent threats from reaching the endpoint.
- Ensures secure access to risky websites without compromising user productivity.
- Reduces the attack surface by keeping web content isolated from the corporate network.
10. Netskope Security Posture Management
- Assesses and manages the security posture of cloud services.
- Identifies misconfigurations and vulnerabilities in cloud environments.
- Provides recommendations for improving cloud security.
These products are designed to work together, providing a comprehensive security solution for organizations that need to protect their data, applications, and users in the cloud.
List of Use Cases where you can use netskope
Netskope can be used in a variety of scenarios to address security and compliance needs in cloud environments. Here are some common use cases:
1. Cloud Data Security
- Use Case: Protecting sensitive data stored in cloud applications.
- Solution: Netskope provides data loss prevention (DLP) capabilities to monitor and protect data across cloud applications, ensuring that sensitive information is not exposed or leaked.
2. Cloud Access Security
- Use Case: Controlling and securing access to cloud applications.
- Solution: Netskope’s CASB (Cloud Access Security Broker) enables organizations to enforce security policies, control user access, and monitor cloud app usage, ensuring that only authorized users can access cloud services.
3. Securing Remote Work
- Use Case: Ensuring secure access to corporate resources for remote workers.
- Solution: Netskope’s Zero Trust Network Access (ZTNA) and Secure Web Gateway (SWG) provide secure access to applications and data, while also protecting against web-based threats, making it easier for employees to work remotely without compromising security.
4. Compliance and Regulatory Requirements
- Use Case: Meeting compliance standards such as GDPR, HIPAA, or PCI-DSS.
- Solution: Netskope’s platform offers visibility into cloud usage, data protection through DLP, and auditing capabilities that help organizations comply with various regulatory requirements.
5. Cloud Threat Protection
- Use Case: Protecting against malware, ransomware, and other advanced threats in the cloud.
- Solution: Netskope Threat Protection includes advanced threat detection and real-time monitoring to protect cloud environments from sophisticated cyber threats.
6. Shadow IT Discovery and Control
- Use Case: Identifying and managing unauthorized cloud applications (Shadow IT) used by employees.
- Solution: Netskope’s CASB helps discover and control the use of unsanctioned cloud services, ensuring that only approved apps are used and that they comply with security policies.
7. Secure Collaboration
- Use Case: Ensuring secure file sharing and collaboration in cloud platforms like Office 365, Google Workspace, etc.
- Solution: Netskope enforces security policies on file sharing and collaboration platforms, ensuring that data is shared securely and only with authorized parties.
8. Network Security Transformation (SASE)
- Use Case: Modernizing network security by integrating security functions directly into the cloud.
- Solution: Netskope’s Secure Access Service Edge (SASE) offers a cloud-native approach to securing network traffic, combining SWG, CASB, and ZTNA into a unified solution for secure and efficient network security.
9. Remote Browser Isolation
- Use Case: Securing web access without exposing the network to potential threats.
- Solution: Netskope Remote Browser Isolation (RBI) allows users to browse the web securely by isolating web content from the endpoint, thus protecting the corporate network from web-based threats.
10. Risk and Compliance Assessment
- Use Case: Assessing and managing the security posture of cloud services.
- Solution: Netskope Security Posture Management helps identify and remediate misconfigurations, vulnerabilities, and compliance risks in cloud environments, ensuring that the cloud infrastructure is secure.
11. Incident Response and Forensics
- Use Case: Investigating and responding to security incidents in the cloud.
- Solution: Netskope provides detailed analytics and reporting that assist security teams in identifying, investigating, and responding to incidents, facilitating faster and more effective incident management.
12. Encryption and Key Management
- Use Case: Encrypting sensitive data in the cloud and managing encryption keys.
- Solution: Netskope offers encryption and key management solutions that allow organizations to encrypt data stored in the cloud and retain control over the encryption keys.
These use cases highlight the versatility of Netskope’s platform in addressing a wide range of cloud security challenges.

Leave a Reply