Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
What is Multi-Factor Authentication (MFA)?
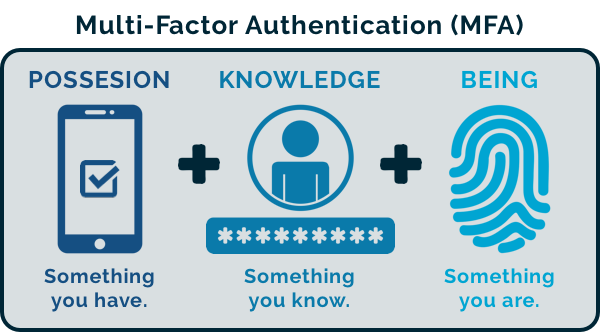
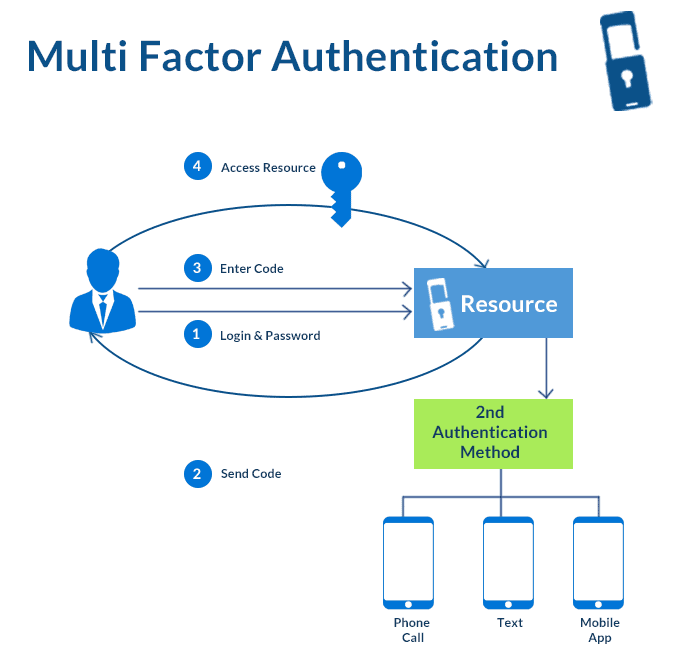
Multi-Factor Authentication (MFA) is a security measure that requires users to provide two or more verification factors to gain access to an application, system, or online account. Unlike traditional single-factor authentication (e.g., passwords), MFA adds additional layers of security by combining:
- Something you know (password or PIN).
- Something you have (a physical token, smartphone app, or smart card).
- Something you are (biometrics such as fingerprint, retina scan, or voice recognition).
MFA ensures that even if one factor is compromised, unauthorized access is less likely, significantly enhancing security.
Why Do We Need Multi-Factor Authentication?
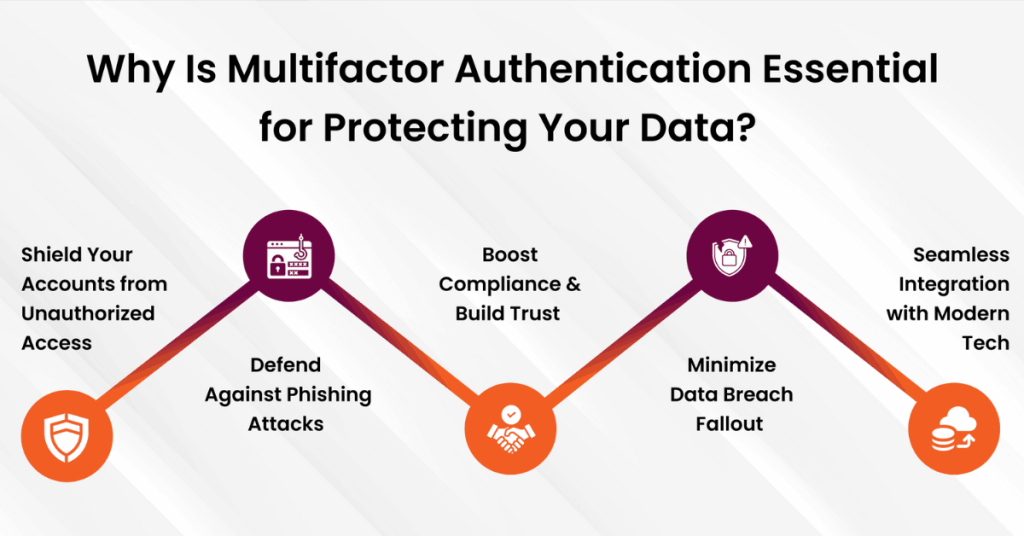
The need for MFA stems from the increasing sophistication of cyber threats and the critical importance of safeguarding sensitive data. Here are the primary reasons:
- Mitigating Password Vulnerabilities: Passwords are often weak, reused, or compromised, making single-factor authentication insufficient.
- Protecting Sensitive Information: Whether personal data or enterprise-level confidential files, MFA prevents unauthorized access.
- Reducing Risks of Phishing Attacks: Even if credentials are stolen through phishing, MFA’s secondary verification blocks unauthorized logins.
- Ensuring Compliance: Many industries (e.g., healthcare, finance) mandate MFA for compliance with regulations like GDPR, HIPAA, and PCI-DSS.
- Securing Remote Workforces: With the rise of remote work, MFA ensures secure access to organizational systems from external networks.
What are the Advantages of Multi-Factor Authentication?
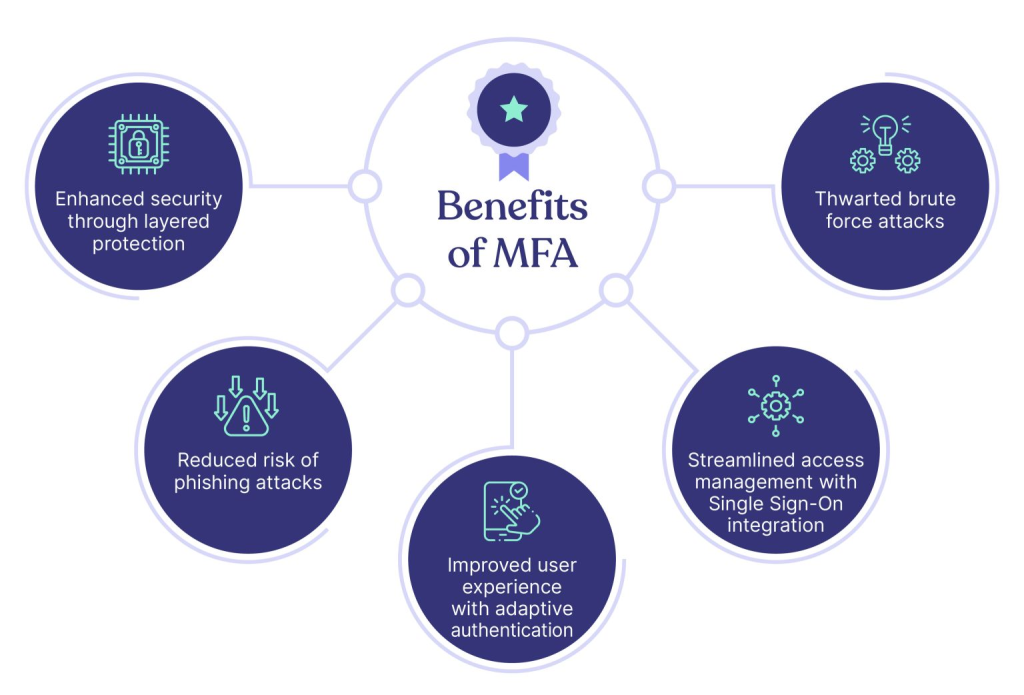
- Enhanced Security: By requiring multiple factors, MFA reduces the risk of unauthorized access even if one factor is compromised.
- Fraud Prevention: Protects against identity theft, phishing, and brute-force attacks.
- Improved Compliance: Helps organizations meet regulatory requirements and avoid penalties.
- User Trust: Builds customer and employee confidence in the system’s security.
- Flexibility in Methods: Provides multiple options for authentication (e.g., SMS, email, biometrics) tailored to user needs.
- Reduced Costs from Breaches: Minimizes the financial and reputational impact of data breaches.
What are the Features of Multi-Factor Authentication Tools?
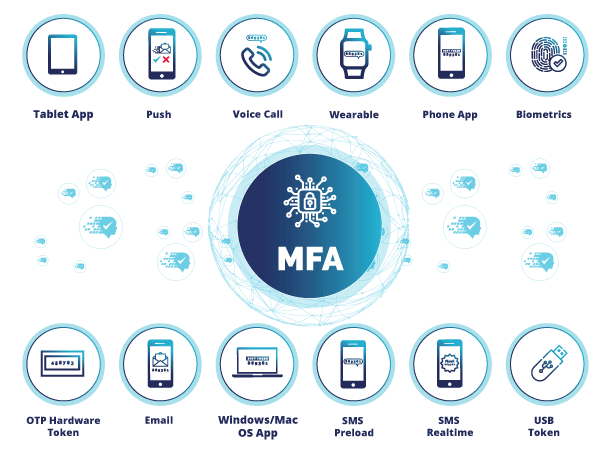
- Variety of Authentication Factors: Support for passwords, OTPs, biometrics, and physical devices.
- Device Compatibility: Integration with desktops, mobile apps, and hardware tokens.
- Adaptive Authentication: Dynamically adjusts security based on user behavior, location, and risk level.
- Seamless Integration: Works with enterprise applications, cloud services, and VPNs.
- User-Friendly Interfaces: Offers intuitive onboarding and authentication processes for end users.
- Reporting and Monitoring: Provides real-time analytics and alerts for suspicious login attempts.
- Offline Authentication: Options to authenticate users in environments without internet access.
- Customizable Policies: Ability to configure security policies based on organizational requirements.
- Failover Mechanisms: Backup methods (e.g., security questions) in case primary methods fail.
- Encryption and Secure Data Storage: Ensures authentication data is protected.
Top 10 Use Cases of Multi-Factor Authentication Tools
- Securing Remote Work Access: Ensures only verified employees can access company networks from remote locations.
- Protecting Cloud-Based Services: Adds extra security for platforms like AWS, Azure, and Google Workspace.
- Safeguarding Financial Transactions: MFA is crucial for online banking, mobile wallets, and payment systems.
- Preventing Unauthorized Device Access: Secures physical devices such as laptops or smartphones.
- Compliance in Regulated Industries: Enforces compliance in industries like healthcare (HIPAA), finance (PCI DSS), and government (FISMA).
- Securing Online Accounts: Protects personal accounts like email, social media, and e-commerce profiles.
- Access Control for Enterprise Applications: Ensures only authorized personnel access CRM, ERP, and HR systems.
- Privileged Access Management: Adds a security layer for administrators and high-privilege accounts.
- Customer Identity Verification: Used by businesses to verify customer identities during onboarding or transactions.
- IoT Device Security: Adds an authentication layer for accessing IoT platforms and devices.
How to Implement Multi-Factor Authentication?
Step 1: Assess Requirements
- Identify critical systems and applications needing MFA.
- Define user groups and authentication factors based on their roles.
Step 2: Choose the Right MFA Tool
- Evaluate tools based on features like compatibility, ease of use, and scalability. Examples include Microsoft Authenticator, Google Authenticator, and Okta.
Step 3: Integrate with Existing Systems
- Connect MFA with identity providers (IdPs) like Active Directory, SAML, or OAuth.
- Ensure compatibility with all critical applications.
Step 4: Configure Authentication Methods
- Set up authentication factors such as biometrics, OTPs, or hardware tokens.
- Enable fallback options (e.g., recovery codes) for accessibility.
Step 5: Enforce Security Policies
- Define policies for high-risk scenarios (e.g., logins from unknown devices or locations).
- Implement adaptive authentication for dynamic responses.
Step 6: Educate Users
- Provide training on using MFA tools effectively.
- Communicate the importance of MFA to minimize resistance.
Step 7: Monitor and Optimize
- Track login attempts and monitor for suspicious activity.
- Regularly update MFA tools to address vulnerabilities and improve features.


