Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
Data Loss Prevention (DLP) is a critical component of modern cybersecurity strategies, designed to safeguard sensitive information from unauthorized access, use, or transmission. DLP tools play a vital role in protecting an organization’s valuable data assets, ensuring compliance with regulations, and maintaining a competitive edge. Let’s delve into the detailed concept of DLP tools and their characteristics.
Understanding Data Loss Prevention (DLP)
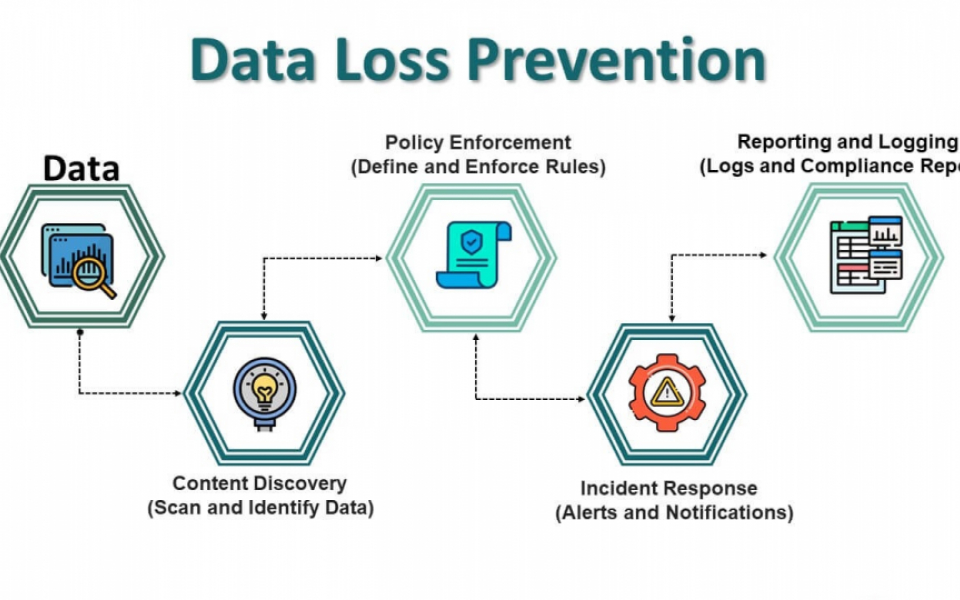
Data Loss Prevention refers to a set of tools, technologies, and processes that detect, monitor, and protect sensitive data across an organization’s network, endpoints, and cloud environments. The primary goal of DLP is to prevent data breaches, leaks, and unauthorized access to critical information.
Key Objectives of DLP
- Data Protection: Safeguarding sensitive information from theft, loss, or misuse.
- Compliance: Ensuring adherence to regulatory requirements such as GDPR, HIPAA, and PCI-DSS.
- Visibility: Providing insights into data movement and usage across the organization.
- Risk Mitigation: Reducing the likelihood of data breaches and associated financial and reputational damages.
Types of DLP Solutions
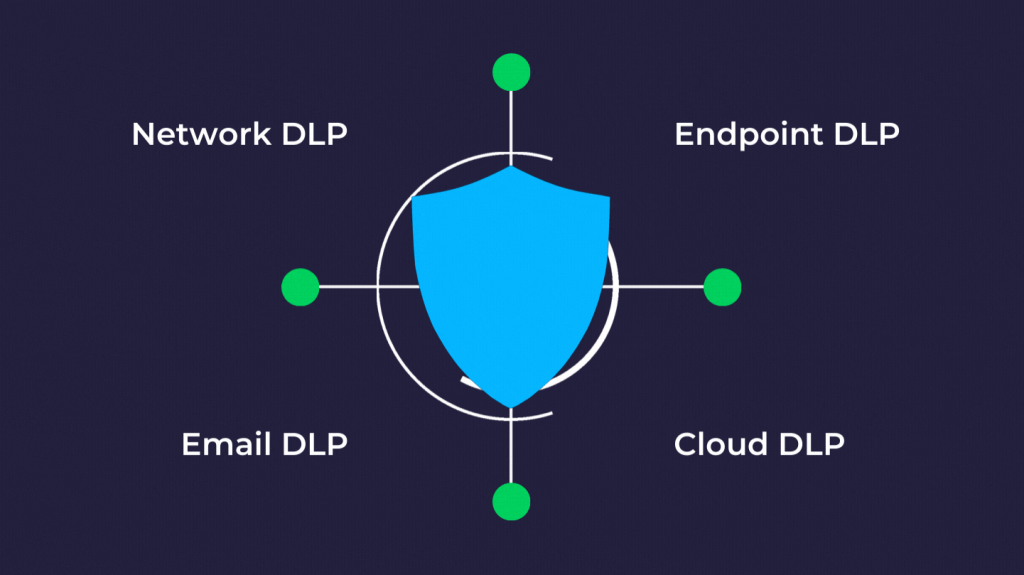
DLP tools can be categorized based on their deployment and focus:
Endpoint DLP
Endpoint DLP solutions protect data on individual devices such as laptops, desktops, and servers3. These tools:
- Monitor data copying, pasting, and transferring from devices
- Implement content inspection and contextual analysis
- Enforce policies on endpoints to prevent unauthorized data transfers
Network DLP
Network DLP focuses on monitoring data flowing across the organization’s network3. Key features include:
- Detecting and blocking unauthorized data transfers through email, file sharing, or web browsing
- Analyzing network traffic for sensitive data patterns
- Enforcing policies on data in transit
Cloud DLP
Cloud DLP solutions protect data stored in cloud services, including3:
- Cloud storage repositories
- Cloud databases
- SaaS applications
These tools monitor data access, transfer, and usage within cloud environments.
Advanced Features of Modern DLP Solutions
AI and Machine Learning Integration
Modern DLP tools are increasingly leveraging artificial intelligence and machine learning to enhance their capabilities1:
- Improved accuracy in detecting potential data breaches
- Adaptive learning to evolve with changing threats and data usage patterns
- Reduction of false positives, enhancing overall effectiveness
Real-time Monitoring and Analysis
DLP solutions now offer sophisticated real-time monitoring capabilities3:
- Continuous monitoring of data in use, at rest, and in transit
- Analysis of data across various locations, including endpoints, servers, networks, and cloud services
- Complex pattern-matching and statistical analysis of data activity
Cloud Integration
With the increasing adoption of cloud services, DLP tools have expanded their reach9:
- Protection for cloud storage repositories and SaaS applications
- Monitoring of data access, transfer, and usage within cloud environments
- Unified policies across on-premises and cloud infrastructures
Implementation Best Practices
1. Data Discovery and Classification
Before implementing DLP policies, it’s crucial to understand your data landscape10:
- Identify and classify sensitive data across your organization
- Use automated tools to discover and inventory confidential information
- Implement data tagging and labeling for easier management
2. Policy Creation and Enforcement
Developing effective DLP policies is a critical step3:
- Create granular policies based on data security requirements and regulatory compliance needs
- Enforce policies consistently across all monitored channels
- Regularly review and update policies to address evolving threats and business needs
3. Employee Training and Awareness
The human element is crucial in preventing data loss15:
- Conduct regular training sessions on data security best practices
- Use real-world examples to illustrate potential risks and consequences
- Foster a culture of data protection awareness throughout the organization
4. Incident Response and Remediation
Having a robust incident response plan is essential3:
- Set up automated alerts for potential policy violations
- Implement immediate response actions such as blocking transfers or quarantining files
- Establish clear procedures for investigating and remediating data loss incidents
Case Studies and Success Stories
Cloudflare’s Thanksgiving Cyberattack (2023)20
Cloudflare successfully thwarted a major cyberattack attempt:
- An intruder exploited stolen credentials to access Cloudflare’s Atlassian server
- Cloudflare’s Zero Trust architecture prevented further network traversal and data compromise
- The company responded by rotating over 5,000 production credentials and triaging nearly 5,000 computers
Omni American Bank DLP Implementation17
A Texas-based bank implemented a comprehensive DLP solution:
- The bank sought greater visibility into data usage and movement
- They chose Websense (now part of Forcepoint) as their DLP provider
- The solution helped detect and prevent unauthorized transmission of sensitive information
Emerging Trends in DLP
Integration with Other Security Tools
DLP solutions are increasingly being integrated with other security technologies11:
- Security Information and Event Management (SIEM) systems
- Identity and Access Management (IAM) platforms
- Encryption tools and Digital Rights Management (DRM) solutions
User and Entity Behavior Analytics (UEBA)
DLP tools are incorporating UEBA capabilities to:
- Establish baseline behavior for users and entities
- Detect anomalous activities that may indicate insider threats or compromised accounts
- Provide context-aware security measures
Advanced Capabilities of DLP Tools
Machine Learning and AI Integration
Many modern DLP tools incorporate machine learning and artificial intelligence to:
- Improve accuracy in detecting potential data breaches
- Adapt to evolving threats and data usage patterns
- Reduce false positives and enhance overall effectiveness
User and Entity Behavior Analytics (UEBA)
DLP solutions often include UEBA capabilities to:
- Establish baseline behavior for users and entities
- Detect anomalous activities that may indicate insider threats or compromised accounts
- Provide context-aware security measures
Integration with Other Security Tools
DLP tools can integrate with various security solutions, including:
- Security Information and Event Management (SIEM) systems
- Identity and Access Management (IAM) platforms
- Encryption tools and Digital Rights Management (DRM) solutions
Implementing DLP: Best Practices
To maximize the effectiveness of DLP tools, organizations should consider the following best practices:
- Develop a Comprehensive DLP Policy: Create a clear policy framework aligned with the organization’s broader security strategy1.
- Prioritize Data Classification: Identify and categorize sensitive data to focus protection efforts effectively1.
- Implement in Phases: Start with critical data and gradually expand coverage to avoid overwhelming the system and users.
- Provide User Training: Educate employees about DLP policies and their role in protecting sensitive data.
- Regularly Update and Refine: Continuously review and adjust DLP policies and rules to address evolving threats and business needs.
- Monitor and Analyze: Regularly review DLP logs and reports to identify trends and areas for improvement.
By implementing robust DLP tools and following best practices, organizations can significantly enhance their data security posture, reduce the risk of data breaches, and maintain compliance with regulatory requirements.



