devsecopsnow@gmail.com
-

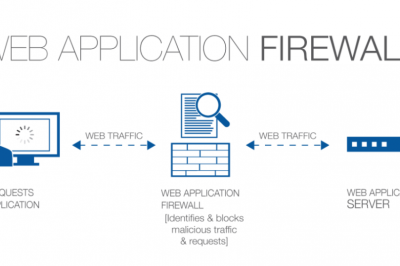
How to get Certified Devsecops Engineer?
This thorough training program provides individuals with the necessary skills and expertise to become Certified DevSecOps Engineers. Learn how to…
-
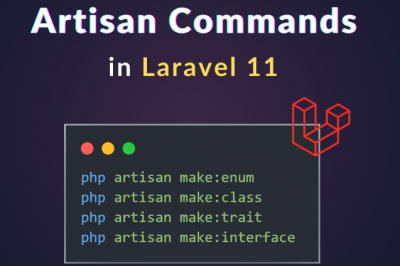
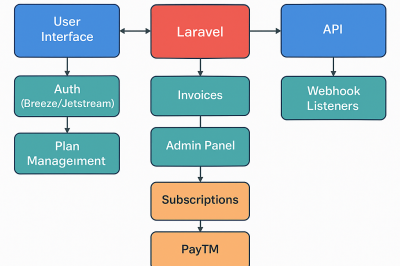
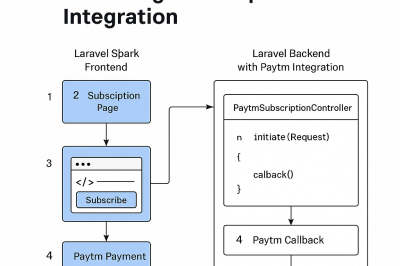
Laravel 11 – New Artisan commands
The most recent stable release of Laravel is version 11, which has been publicly accessible since March 12, 2024. Laravel…
-

What are the data provided by Linkedin API?
The data accessibility environment is always changing, especially when it comes to social networking platforms, therefore it’s important to know…
-
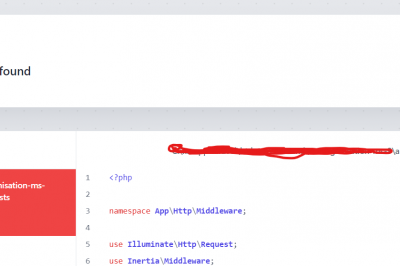
Class “Inertia\Middleware” not found
Getting this Error:- Solution:- Step 1:- You just need to run a composer command in your project which i have…
-

How to upgrade you Laravel project in Laravel 10 version?
In this article I’m going to share my learnings related to Laravel Projects. For every new major version, Laravel’s documentation…
-

Git all Commands
Git commands along with a brief description of what they do: Depending on your unique requirements and workflow, there are…
-
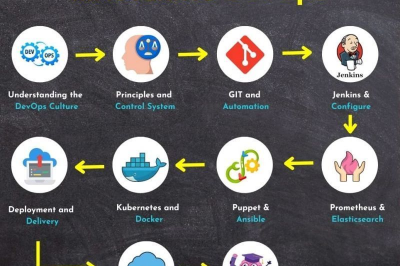
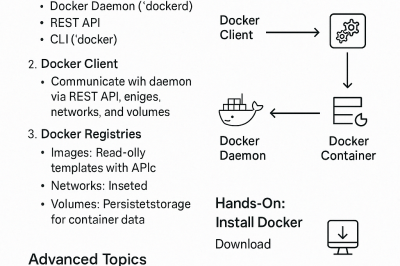
𝗠𝗮𝘀𝘁𝗲𝗿𝗶𝗻𝗴 𝗗𝗲𝘃𝗢𝗽𝘀: 𝗔 𝗥𝗼𝗮𝗱𝗺𝗮𝗽 𝘁𝗼 𝗦𝘂𝗰𝗰𝗲𝘀𝘀
1. Foundational Understanding 2. Continuous Integration (CI) 3. Infrastructure as Code (IaC) 4. Containerization and Orchestration 5. Continuous Deployment (CD)…
-
Class “Anhskohbo\NoCaptcha\NoCaptchaServiceProvider” not found
Error :- Error Code :- Solution:- Step 1 :- Go to your project terminal and eun the following code which…
-

ERROR: Declaration of App\Services\CustomPasswordBroker
Error: Solution: Step – 1 – Go to your Laravel 10 project. Step – 2 – find the file named…