devsecopsnow@gmail.com
-

Top Server Management Tools: Exploring Alternatives to Mobaxterm for Enhanced Server Control and Administration
Depending on your unique requirements and tastes, you have a few options when searching for server management alternatives to Mobaxtream….
-

What is PHP and use cases of PHP?
What is PHP? Are you curious in PHP’s definition and operation? There’s nowhere else to look! The ins and outs…
-
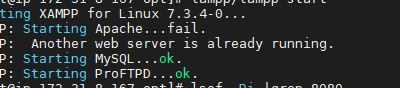
XAMPP: Starting Apache…fail. XAMPP: Another web server is already running.
Error:- When You get this error You don’t need to panic. Just Follow my commands and instruction you will get…
-

PHP for Beginners: Everything You Need to Know to Get Started
What is PHP? The popular server-side programming language PHP, or Hypertext Preprocessor, is mostly used for web development. It’s well…
-

What is Qualys?
What is Qualys Qualys is a cloud security company that provides a variety of security and compliance solutions to businesses…
-

Top 𝐀𝐖𝐒 𝐰𝐢𝐭𝐡 𝐝𝐞𝐯𝐨𝐩𝐬 𝐫𝐨𝐥𝐞 𝐢𝐧𝐭𝐞𝐫𝐯𝐢𝐞𝐰𝐬 Questions:-
1. What is GIT stash ?2. What is a branching strategy?3. What is the command to discard changes in the…
-
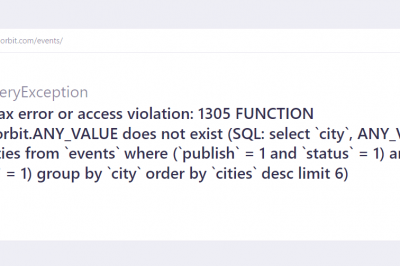
Syntax error or access violation: 1305 FUNCTION
Error:- Solution:- Step 1:- Go inside your laravel project. Step 2:- Open the File named database.php which is present in…
-

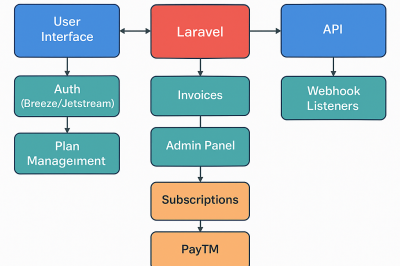
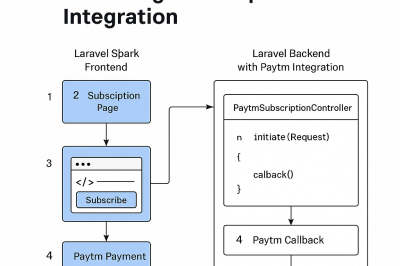
What is Difference between Laravel and Laravel Livewire?
One prominent PHP web framework that is well-liked for both its rich feature set and attractive syntax is Laravel. It…
-

Master PHP: A Complete Step-by-Step Tutorial for Beginners to Advanced Developers
Thanks for coming to the definitive resource for learning PHP, the flexible and potent programming language that powers a large…
-
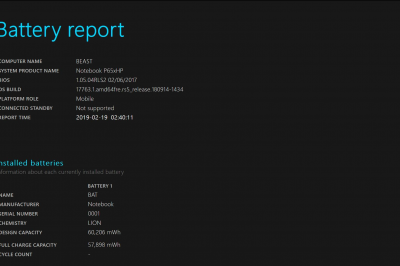
How to Get info of the battery health of your Laptop
Command Prompt may be used to check the status of your laptop’s battery on Windows. Start by launching Command Prompt…