devsecopsnow@gmail.com
-

What is netskope?
Netskope is a cybersecurity company that focuses on cloud security. It provides a platform designed to secure data and protect…
-
Calling livewire function from ajax function of laravel Project
Method 1: Using Livewire Events The Livewire component may handle events that are triggered by JavaScript using this method. This…
-

Guest Posting on Devsecopsnow.com
Dear User, Thank you for reaching out to us with your interest in guest blogging and related services for our…
-

Example job description of DevSecOps Engineer?
Job Overview: We are looking to add a talented DevSecOps Engineer to our vibrant team. The ideal applicant will have…
-

Unveil Chennai: A Guide to Events, Attractions, and Hidden Gems
Chennai, the vibrant and bustling metropolis of Tamil Nadu, is a city where history, culture, and modernity seamlessly blend. Whether…
-

MySQL: List of Comprehensive List of approach to secure MySQL servers.
Securing MySQL servers is crucial to protect your data from unauthorized access and potential breaches. Here is a comprehensive list…
-

Bangalore Orbit: Your Curated Gateway to Unveiling Bengaluru’s Magic
Having analyzed Bangalore Orbit’s website (https://www.bangaloreorbit.com/), I’ve crafted a compelling piece highlighting their products and services. This content emphasizes the…
-
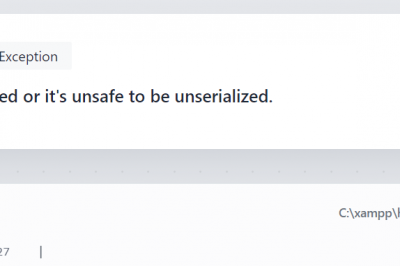
Laravel Error: Your serialized closure might have been modified or it’s unsafe to be unserialized.
Step 1 :- Go to your Project Terminal. Step 2:- Run the following command one by one and your issue…
-
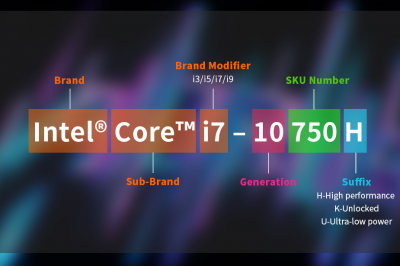
Laptop Processor Suffixes Decoded: Choose the Right One for Your Needs
The letters at the end of a laptop processor’s model number typically indicate the processor’s performance characteristics and target usage….
-
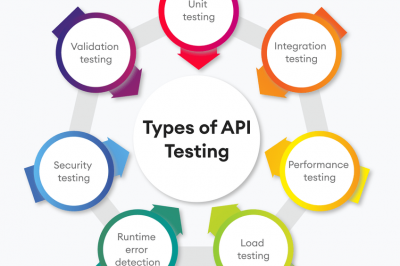
9 Essential Types of API Testing: A Comprehensive Guide to Ensure Secure and Reliable APIs
Introduction to API Testing APIs, or application programming interfaces, are now essential for smooth communication between various software systems in…