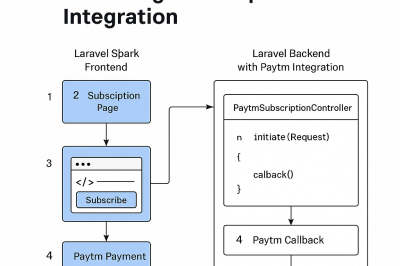
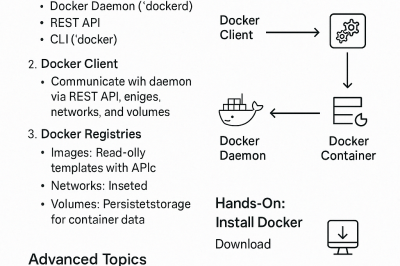
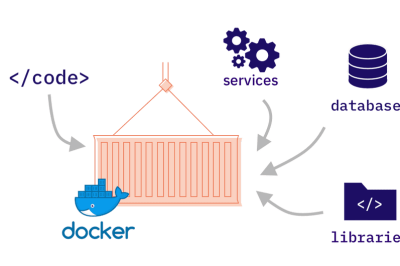
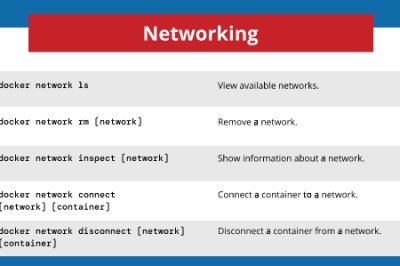
devsecopsnow@gmail.com
-

Explore Firozabad Conveniently: Bike and Car Rentals Made Simple with Motoshare
Known as the Glass City of India, Firozabad is a hub of culture, art, and vibrant history. To make your…
-

Discover Cuttack Hassle-Free: Bike and Car Rentals Made Easy with Motoshare
Cuttack, known for its rich cultural heritage and bustling city life, offers travelers an experience like no other. To help…
-

Explore Warangal Your Way: Convenient Bike and Car Rentals with Motoshare
Are you planning a trip to Warangal? Motoshare’s newly launched bike and car rental services make exploring this historic city…
-

Explore Noida Effortlessly: Convenient Bike and Car Rentals with Motoshare
Whether you’re visiting Noida for leisure, work, or a quick getaway, having your own transportation makes all the difference. Motoshare’s…
-

Discover Bikaner at Your Own Pace: Hassle-Free Bike and Car Rentals with Motoshare
Are you planning to visit the vibrant city of Bikaner? Motoshare is here to elevate your travel experience with its…
-

Explore Gwalior with Ease: Top Bike and Car Rental Solutions from Motoshare
Planning to explore the historic city of Gwalior? Motoshare is here to make your journey comfortable and hassle-free. With its…
-

Explore Aligarh with Motoshare: Hassle-Free Bike and Car Rentals for Every Journey
Aligarh, a city renowned for its rich cultural heritage and academic significance, offers plenty to explore for both locals and…
-

Discover Salem with Motoshare: Convenient Bike and Car Rentals at Your Fingertips
Salem, a city rich in heritage and surrounded by scenic landscapes, is an ideal destination for travelers seeking cultural experiences…
-

Explore Bhubaneswar with Motoshare: Effortless Bike and Car Rentals for Your Adventures
Bhubaneswar, fondly known as the “City of Temples,” is a beautiful blend of history, culture, and modernity. Whether you are…
-

Explore Tiruppur with Motoshare: Your Go-To Bike and Car Rental Platform
Tiruppur, famously known as the “Textile City of India,” offers more than just its industrial charm. It’s a city rich…