Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
Accessing AWS Secret Manager secrets in Kubernetes clusters!
AWS Secret Manager is a fully managed service that makes it easy to store, manage, and retrieve secrets. Kubernetes is an open-source container orchestration system that automates the deployment, scaling, and management of containerized applications.
You can use AWS Secret Manager secrets in Kubernetes clusters in a few different ways:
- Using the AWS Secrets and Configuration Provider (ASCP). The ASCP is a plugin for the Kubernetes Secrets Store CSI Driver that allows you to mount secrets from AWS Secret Manager into pods as files. This is the recommended way to use AWS Secret Manager secrets in Kubernetes clusters.
- Using the AWS SDK for Kubernetes. The AWS SDK for Kubernetes provides a set of APIs that you can use to programmatically access AWS Secret Manager secrets from your pods.
- Using the AWS CLI. You can also use the AWS CLI to access AWS Secret Manager secrets from your pods.
Here are the steps on how to use the ASCP to mount AWS Secret Manager secrets into pods as files:
- Create an IAM role that allows your pods to access AWS Secret Manager secrets.
- Create a SecretProviderClass that specifies the name of the IAM role and the name of the AWS Secret Manager secret that you want to mount into your pods.
- Create a Pod that uses the SecretProviderClass that you created.
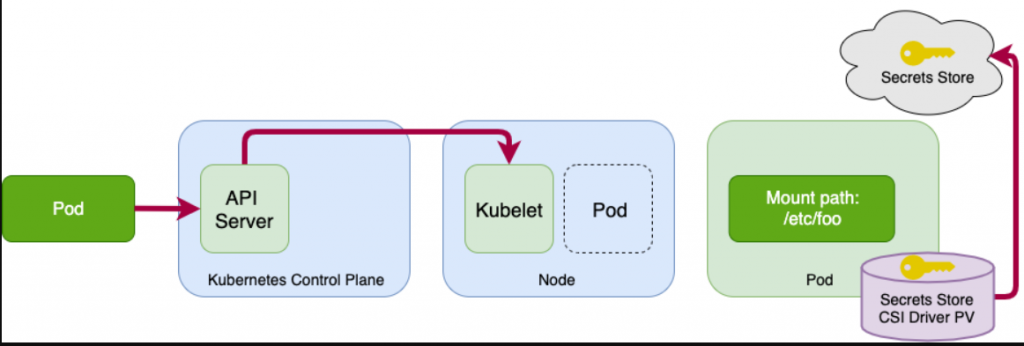
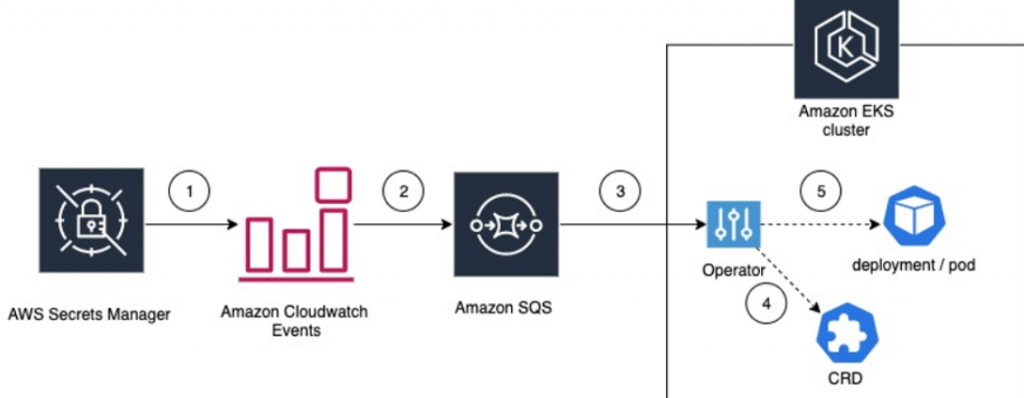
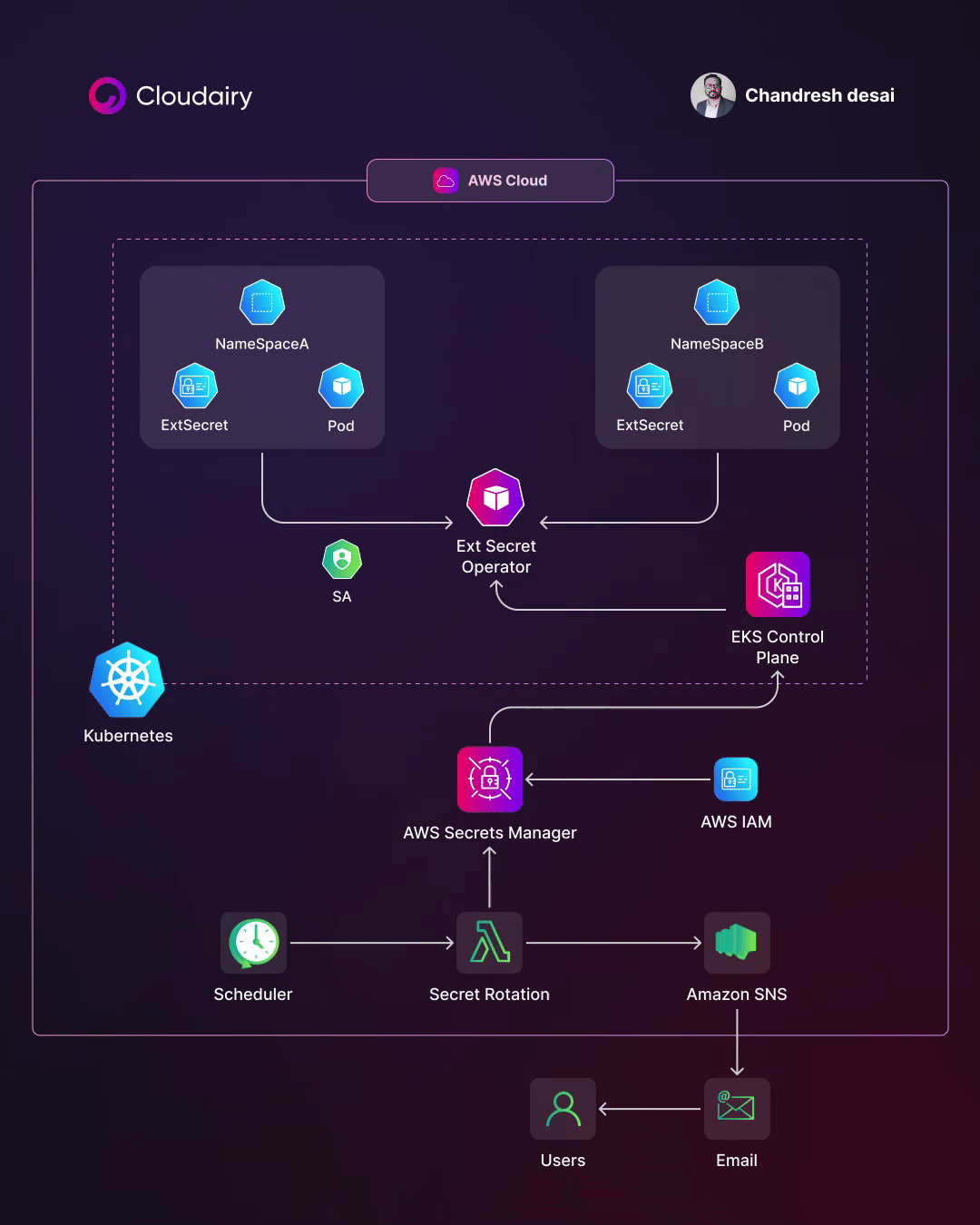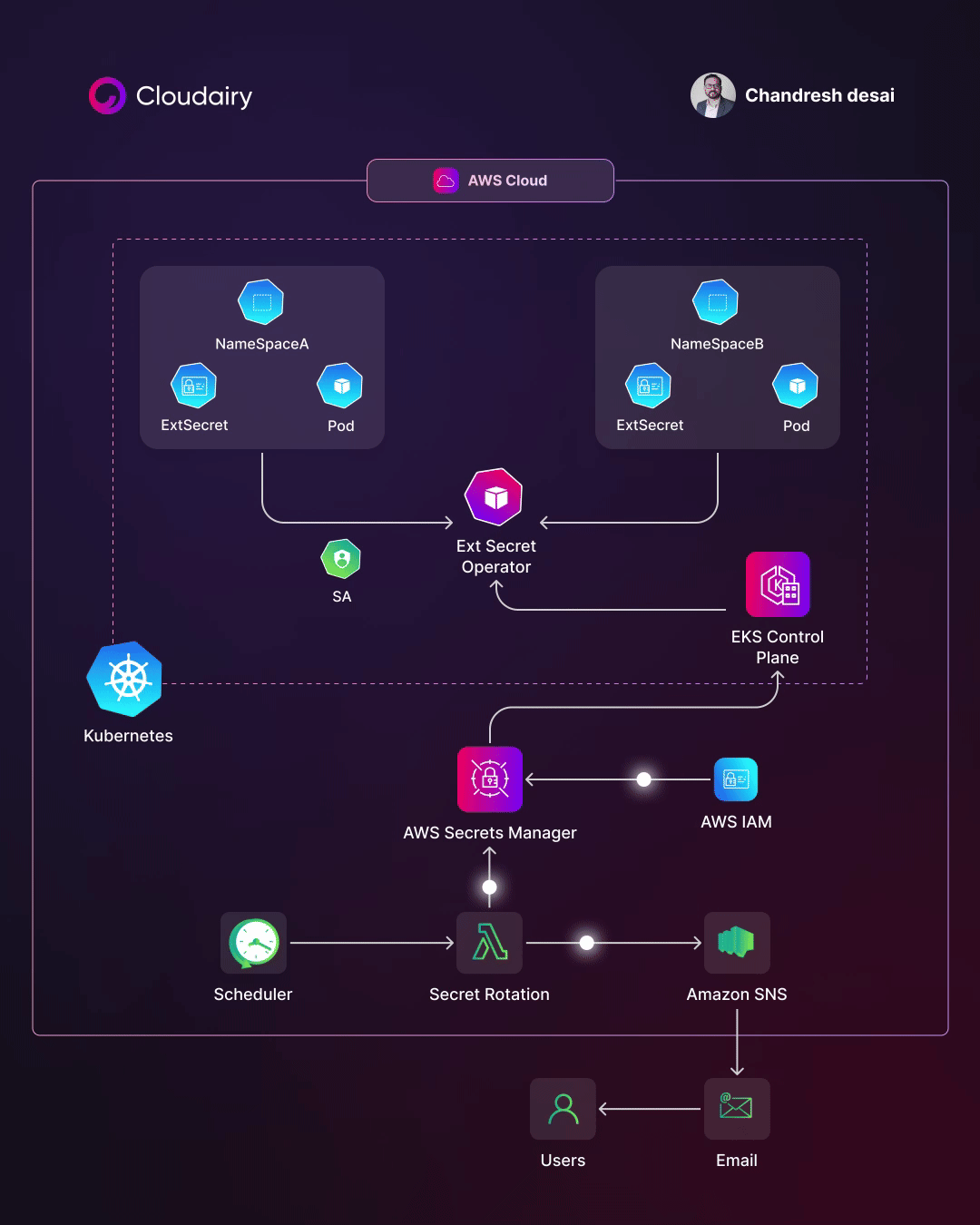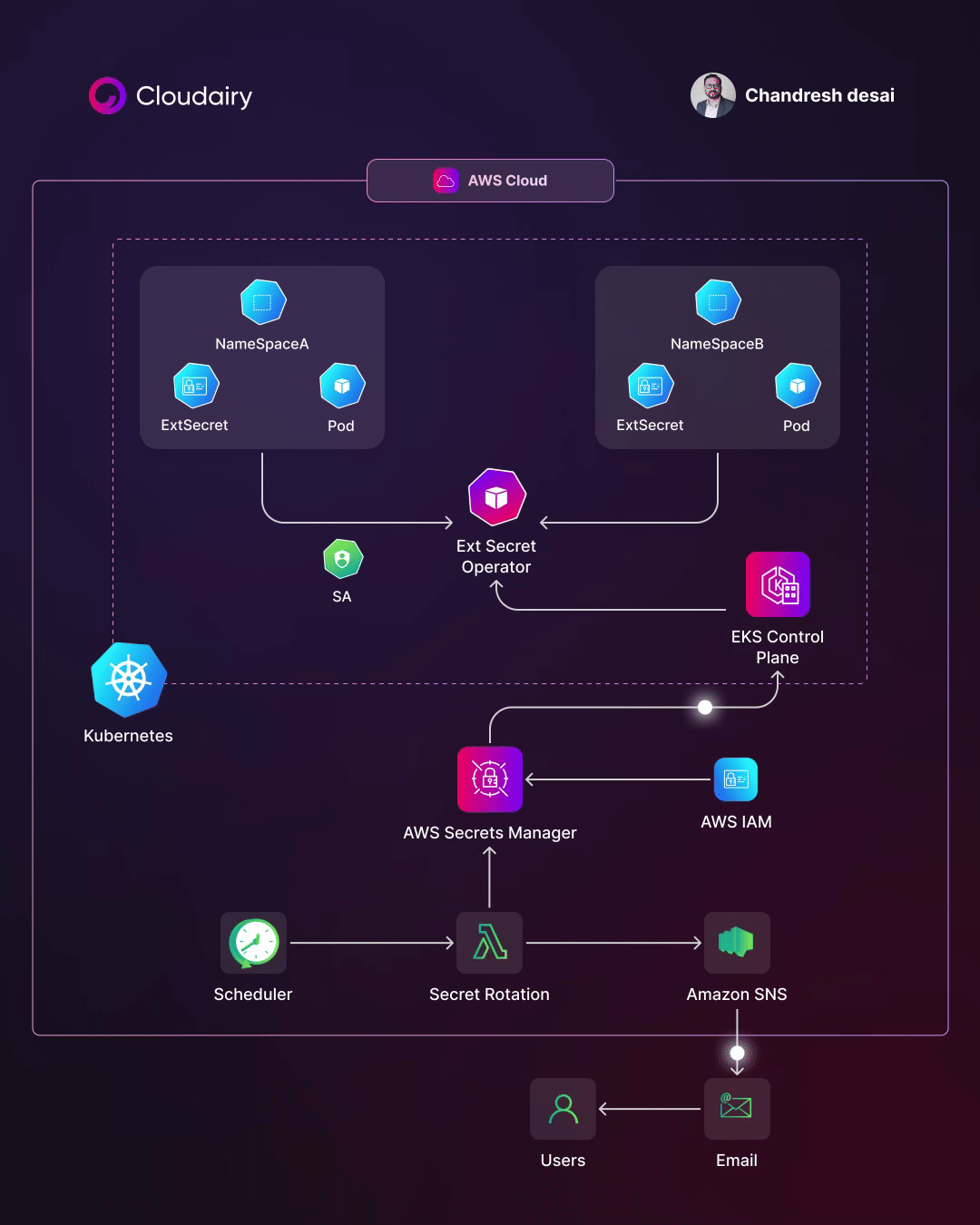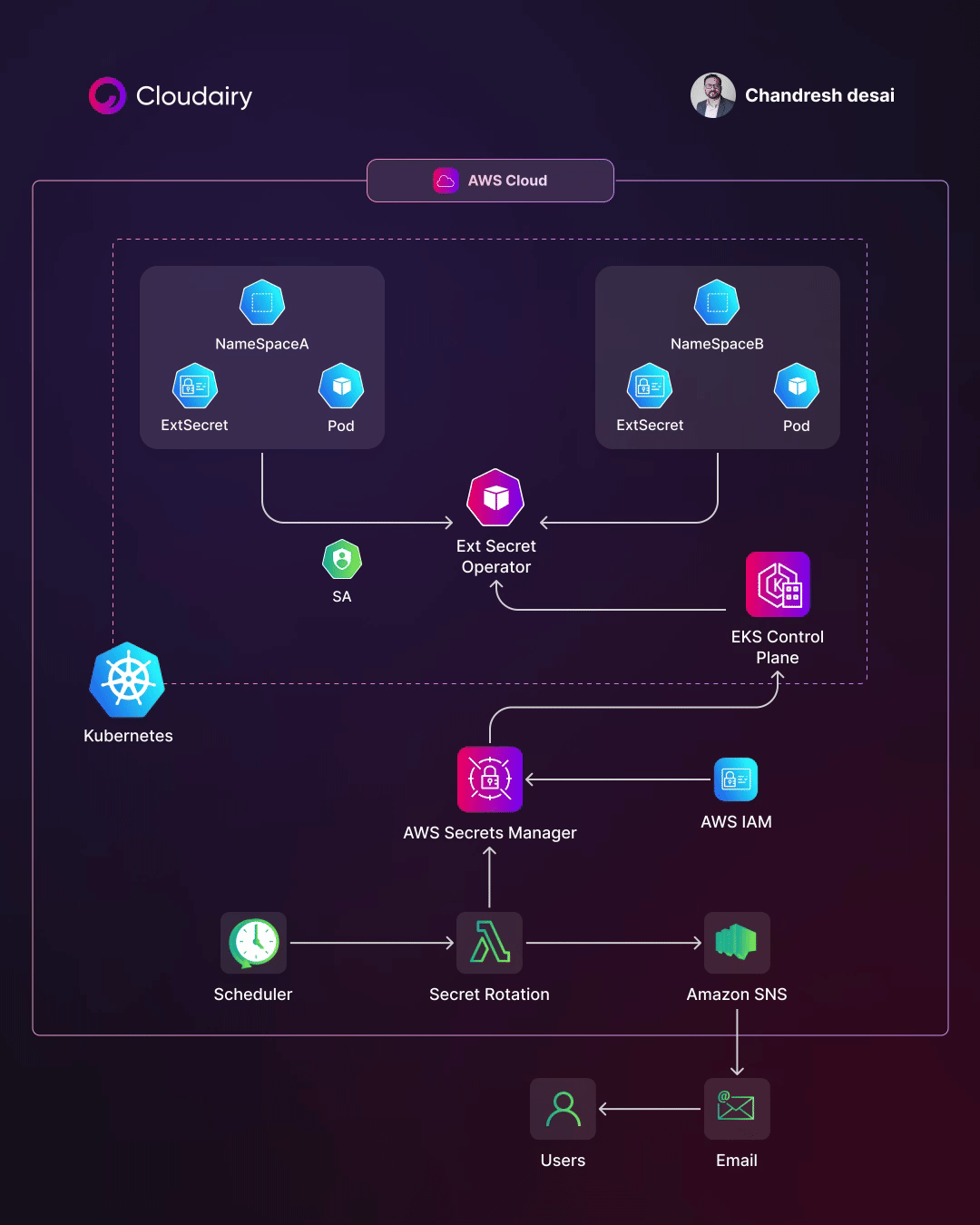
AWS Secret Manager is a secure, centralized, and automated way to manage secrets in Kubernetes clusters. To access and mount secrets from AWS Secret Manager in Kubernetes clusters, you can follow these steps:
1️⃣Create an AWS Secrets Manager secret or a parameter in the AWS Systems Manager Parameter Store.
2️⃣Create an IAM role for a Service Account (IRSA) that allows access to the secret or parameter you created in step 1.
3️⃣Create a Kubernetes SecretProviderClass object that specifies the AWS Secret Manager secret or AWS Systems Manager Parameter Store parameter you want to mount in your pod.
4️⃣Create a Kubernetes Deployment or Pod object that mounts the SecretProviderClass object you created in Step 3.
5️⃣The Kubernetes pod will now have access to the secret or parameter you mounted in step 4.
Let’s have a look at some of the advantages of using a secrets management solution on EKS:
✅Security: Secrets are encrypted at rest and in transit, and access to secrets is controlled by IAM roles. This helps to protect secrets from unauthorized access.
✅Centralization: Secrets management is centralized, making it easier to track and manage secrets.
✅Automation: Secrets can be rotated automatically, which helps to ensure that secrets are always up-to-date and that they are not compromised.
✅Compliance: AWS Secret Manager is compliant with a variety of security standards, such as SOC 2, ISO 27001, and PCI DSS. This can help you to meet compliance requirements for your Kubernetes clusters.
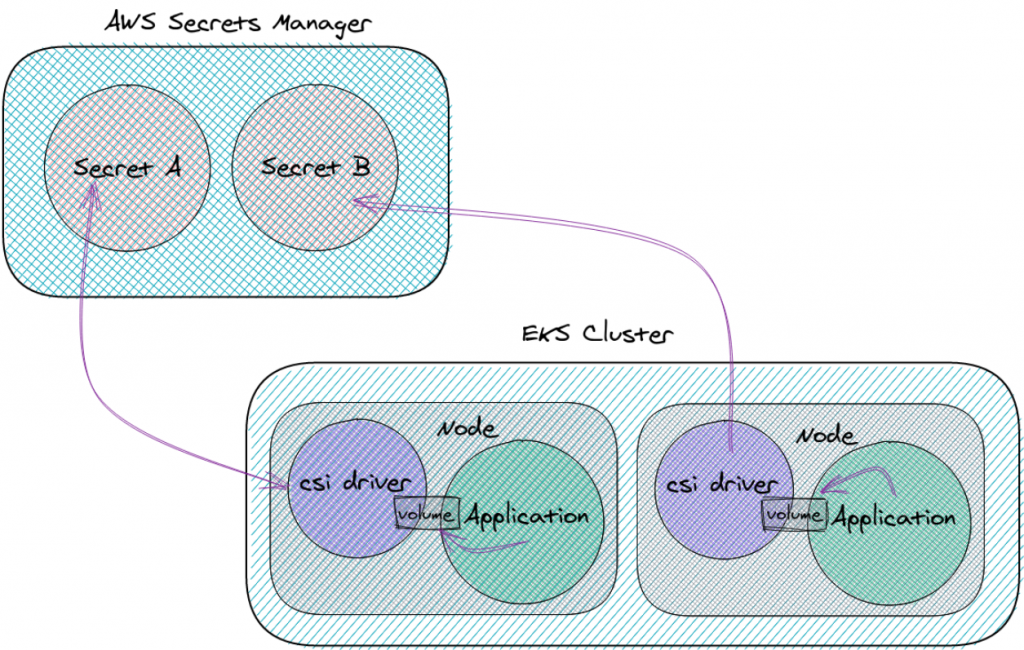
Apart from secure secrets storage, AWS Secrets Manager also provides:
🎯Automatic secrets rotation: Secrets Manager rotates your secrets on a schedule to prevent unauthorized access.
🎯Automatic replication to multiple regions: Secrets Manager replicates your secrets to multiple regions for availability and disaster recovery.
🎯Programmatic secrets retrieval: Secrets Manager provides an API to programmatically retrieve secrets, so you don’t have to hard-code them in your application code.
🎯Integration with other AWS services: Secrets Manager integrates with many AWS services, making it easy to manage secrets for your EKS cluster and other AWS applications.
If you are looking for a secure, centralized, and automated way to manage secrets in your EKS cluster, then AWS Secrets Manager is a great option.
The following is an example of a SecretProviderClass that you can use to mount the my-secret secret from AWS Secret Manager into your pods:
This Pod will mount the my-secret secret from AWS Secret Manager into the /etc/secret-volume directory. The secrets from the my-secret secret will be available to the my-container container as environment variables.
For more information on how to use AWS Secret Manager secrets in Kubernetes clusters, please refer to the following documentation:
- Using AWS Secret Manager secrets with Kubernetes: https://docs.aws.amazon.com/eks/latest/userguide/manage-secrets.html
- AWS Secrets and Configuration Provider (ASCP): https://docs.aws.amazon.com/secretsmanager/latest/userguide/integrating_csi_driver.html



