Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
Introduction
DevSecOps is a set of practices that aims to integrate security (Sec) into the DevOps process. DevOps is a software development approach that emphasizes collaboration and communication between development (Dev) and IT operations (Ops) teams to automate the process of software delivery and infrastructure changes. DevSecOps extends this approach by including security as an integral part of the development and operations workflows.
What is DevSecOps?
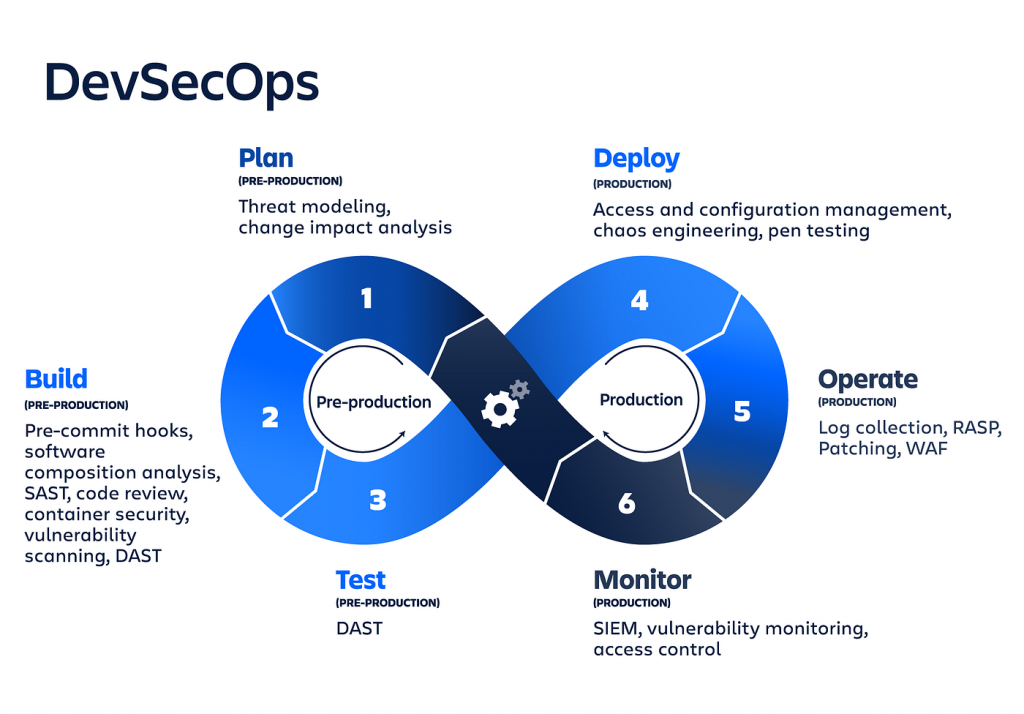
DevSecOps is a collaborative and innovative approach to software development that integrates security practices seamlessly into the DevOps pipeline. It encompasses a set of principles and practices aimed at fostering a culture of continuous security throughout the software development lifecycle. By shifting security measures leftward, DevSecOps ensures that security considerations are woven into the fabric of planning, designing, coding, and deploying applications. This involves automated security testing, compliance checks, and governance procedures, all orchestrated in tandem with development and operations activities. The approach emphasizes constant vigilance through monitoring and rapid incident response, thus fortifying applications against potential threats. By championing shared responsibility and cross-team communication, DevSecOps fundamentally transforms how organizations safeguard their software assets, resulting in more resilient, secure, and reliable systems.
Why We need DevSecOps?
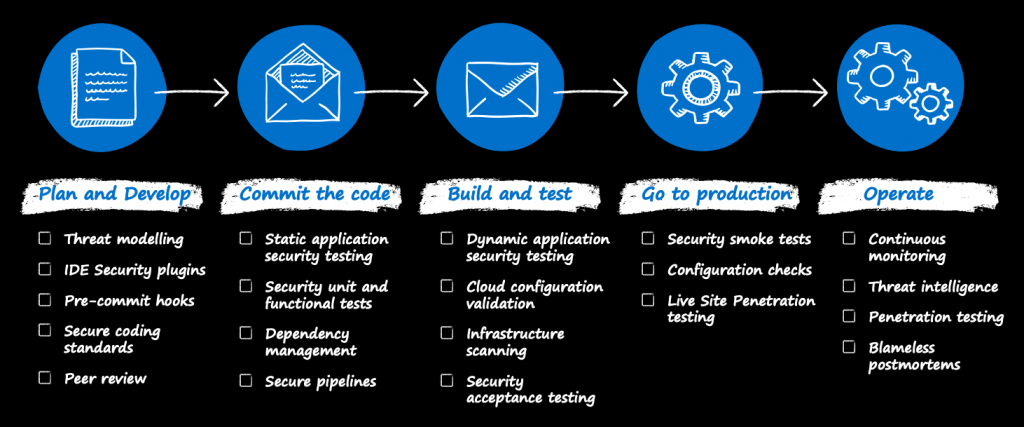
DevSecOps is essential in today’s rapidly evolving technological landscape because it addresses the critical need for security to keep pace with the speed of modern software development. Traditional security measures often lag behind the rapid deployment cycles of DevOps, leaving applications vulnerable to emerging threats. By integrating security practices early and continuously throughout the development process, DevSecOps ensures that security is not an afterthought but an integral part of the software’s DNA. This proactive approach reduces the likelihood of security breaches and vulnerabilities slipping through the cracks. Moreover, it promotes a culture of shared responsibility, where everyone involved in the development process actively participates in safeguarding the software. Ultimately, DevSecOps leads to more robust, resilient, and secure applications that can adapt to the ever-changing threat landscape.
- Rapid Development and Deployment: In today’s fast-paced tech environment, software development and deployment cycles have become incredibly swift. DevSecOps ensures that security measures keep pace with this speed, preventing vulnerabilities from being introduced due to rushed or overlooked security checks.
- Early Detection of Vulnerabilities: Integrating security into the development process from the outset allows for the early identification and rectification of security vulnerabilities. This “shift-left” approach reduces the likelihood of security issues arising in later stages, saving time, effort, and potential reputational damage.
- Improved Collaboration and Communication: DevSecOps fosters a culture of collaboration between development, operations, and security teams. This shared responsibility ensures that security considerations are embedded in every aspect of the development process, leading to more secure and resilient applications.
- Automated Security Measures: DevSecOps promotes the use of automated security testing and compliance checks. This not only increases the efficiency of security processes but also helps in maintaining consistent security standards across all phases of development.
- Compliance and Regulatory Requirements: Many industries have stringent compliance and regulatory requirements regarding data protection and security. DevSecOps assists in automating and ensuring adherence to these standards, reducing the risk of non-compliance and potential legal ramifications.
- Reduction in Security Incidents: By proactively addressing security concerns throughout the development lifecycle, DevSecOps significantly decreases the likelihood of security breaches and incidents. This leads to a more robust and secure software environment.
- Cost-Efficiency: Identifying and fixing security issues earlier in the development process is generally less costly than addressing them after deployment. DevSecOps helps in reducing the financial impact of security incidents and the associated remediation efforts.
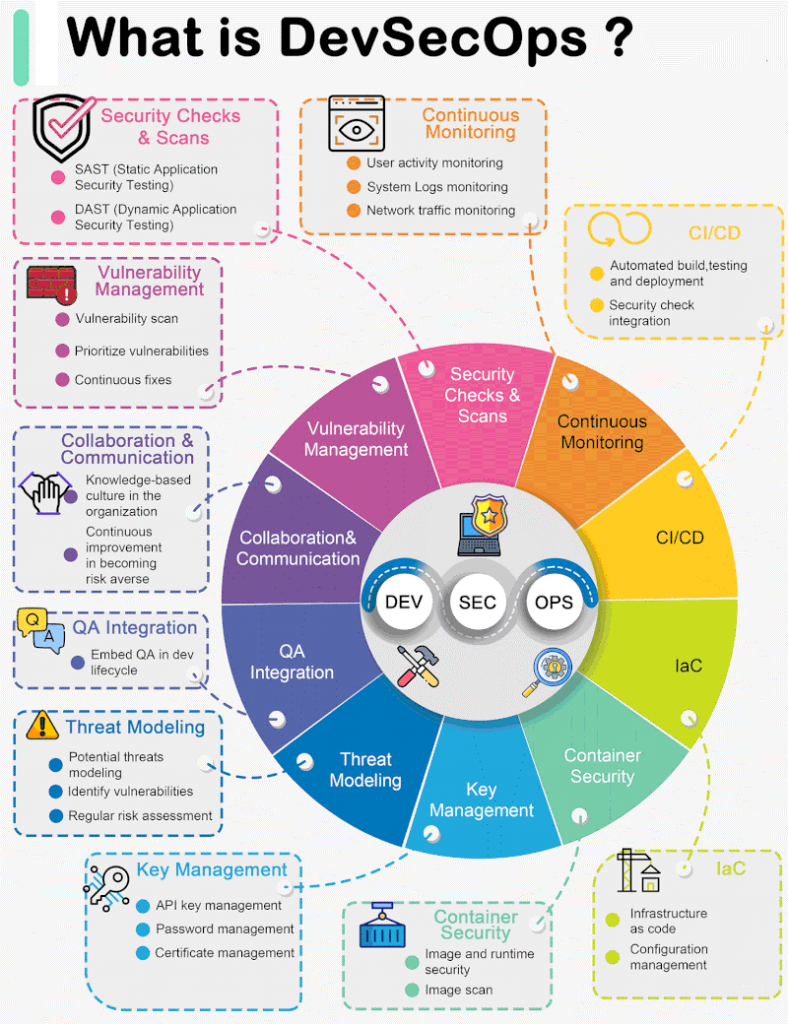
What is the Advantage of DevSecOps?

The primary advantage of DevSecOps lies in its ability to proactively embed security into the heart of the development process. By doing so, it significantly reduces the risk of security vulnerabilities and breaches. This “shift-left” approach means that potential issues are identified and addressed early, saving time, resources, and potential reputation damage. Moreover, the automation of security practices streamlines processes and ensures consistent adherence to security standards. This not only enhances the overall security posture of applications but also fosters a culture of shared responsibility among development, operations, and security teams. Ultimately, DevSecOps leads to more robust, resilient, and secure software systems, capable of withstanding the ever-evolving threat landscape.
- Early Detection of Security Issues: DevSecOps integrates security measures from the very beginning of the development process. This ensures that security vulnerabilities are identified and addressed at an early stage, reducing the likelihood of security breaches in production.
- Faster Response to Security Threats: Automated security testing and continuous monitoring enable rapid identification and response to security threats. This agility is crucial in today’s fast-paced digital landscape where cyber threats evolve rapidly.
- Cost-Effectiveness: Identifying and fixing security issues earlier in the development lifecycle is generally more cost-effective than addressing them after deployment. DevSecOps minimizes the financial impact of security incidents and reduces the cost of remediation.
- Compliance and Regulatory Adherence: Many industries have strict compliance requirements. DevSecOps helps automate compliance checks, ensuring that applications adhere to industry-specific regulations and standards.
- Improved Collaboration: DevSecOps promotes a culture of collaboration between development, operations, and security teams. This shared responsibility for security fosters a stronger and more cohesive working environment.
- Enhanced Trust and Reputation: Security breaches can severely damage an organization’s reputation. DevSecOps helps build trust with customers and stakeholders by demonstrating a commitment to security and data protection.
- Reduced Security Risks: By integrating security practices throughout the development process, DevSecOps significantly reduces the risk of security vulnerabilities and breaches. This leads to more robust and secure applications.
- Consistency and Standardization: DevSecOps encourages the use of automation tools, ensuring that security practices are consistently applied across all stages of development and deployment.
- Flexibility and Adaptability: DevSecOps allows for rapid adaptation to emerging security threats and trends. This flexibility is crucial in a constantly evolving threat landscape.
- Improved DevOps Practices: DevSecOps enhances the overall DevOps process by incorporating security best practices. This leads to a more comprehensive and mature approach to software development and deployment.
What is the feature of DevSecOps?
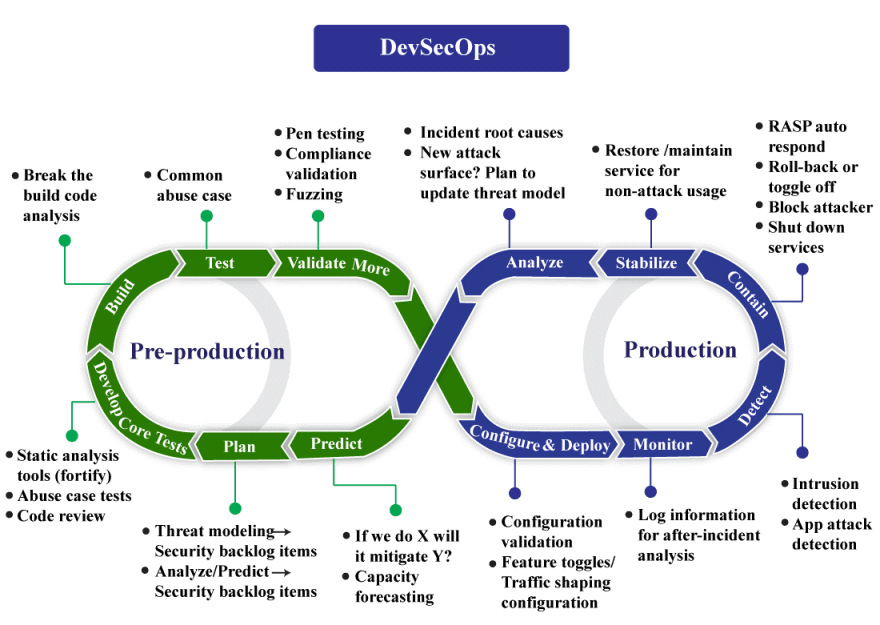
The key features of DevSecOps include its emphasis on early integration of security measures, a shift-left approach that ensures security is considered from the outset of the development process. This enables early detection and resolution of security vulnerabilities. Automation is another pivotal feature, allowing for consistent and efficient security testing, compliance checks, and governance procedures. Collaboration and communication are also central, fostering a culture of shared responsibility among development, operations, and security teams. Continuous monitoring for security threats, along with a rapid incident response capability, ensures applications remain resilient in the face of evolving cyber threats. Additionally, DevSecOps promotes infrastructure as code (IaC), enabling security configurations to be codified and enforced alongside application code, contributing to a more secure and robust deployment process.
- Shift-Left Security: DevSecOps emphasizes integrating security measures from the earliest stages of the software development lifecycle, ensuring security is considered right from the planning and design phases.
- Continuous Security Testing: This feature involves the use of automated security testing tools to scan code and infrastructure for vulnerabilities throughout the development process, allowing for real-time identification and resolution of security issues.
- Automated Compliance and Governance: DevSecOps encourages the automation of compliance checks and the enforcement of security policies, ensuring that applications and infrastructure adhere to industry-specific standards and regulations.
- Collaboration and Communication: DevSecOps promotes strong collaboration and communication between development, operations, and security teams. This facilitates the sharing of knowledge and ensures that security concerns are addressed collectively.
- Continuous Monitoring and Incident Response: DevSecOps advocates for ongoing monitoring of applications and infrastructure for security threats. Additionally, it emphasizes having well-defined incident response processes in place to swiftly address security incidents.
- Infrastructure as Code (IaC): This feature involves managing and provisioning infrastructure using code, allowing for security configurations to be defined and enforced alongside application code, ensuring consistency and security in deployment.
- Shared Responsibility: DevSecOps fosters a culture of shared responsibility for security across development, operations, and security teams, ensuring that everyone takes an active role in identifying and mitigating security risks.
- Flexibility and Adaptability: DevSecOps is designed to adapt to the evolving threat landscape, providing the flexibility to incorporate new security measures and technologies as they emerge.
- Cost-Efficiency: By identifying and addressing security issues early in the development process, DevSecOps can lead to cost savings by minimizing the impact of potential security incidents.
- Enhanced Trust and Reputation: Implementing DevSecOps practices demonstrates a commitment to security and data protection, which can build trust with customers and stakeholders and enhance the organization’s reputation.
What is the Top 10 Use cases of DevSecOps?
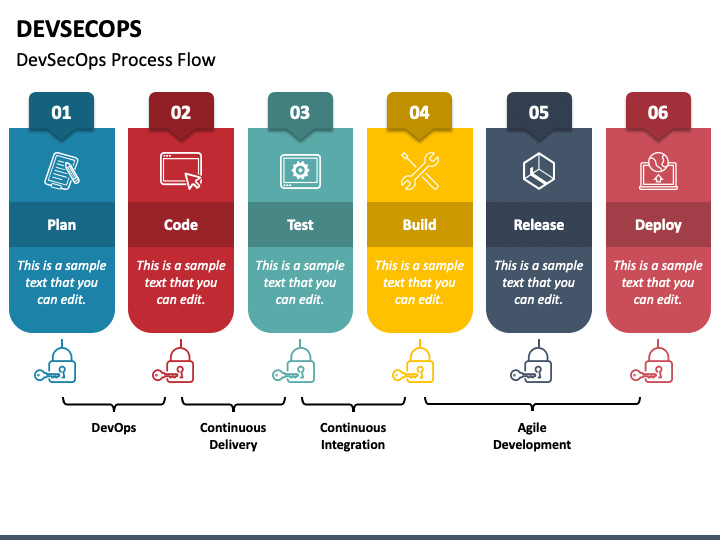
- Automated Security Testing:
- Project Example: Implementing automated static code analysis using tools like SonarQube to scan source code for security vulnerabilities and compliance with coding standards.
- Container Security:
- Project Example: Using container security platforms like Aqua or Twistlock to scan Docker images for vulnerabilities and enforce security policies for containerized applications.
- Continuous Compliance and Governance:
- Project Example: Setting up a compliance automation tool like Chef InSpec or AWS Config to continuously monitor and enforce compliance with industry-specific regulations and organizational policies.
- Vulnerability Management:
- Project Example: Employing vulnerability management tools like Qualys or Nessus to regularly scan networks and applications for known vulnerabilities, prioritizing and addressing them in real-time.
- Secrets Management:
- Project Example: Integrating a secrets management tool like HashiCorp Vault to securely store and manage sensitive information (e.g., API keys, passwords) used in applications and infrastructure.
- Security Information and Event Management (SIEM):
- Project Example: Deploying a SIEM solution like Splunk or ELK Stack to aggregate, correlate, and analyze security events and logs from various sources for early threat detection.
- Incident Response Automation:
- Project Example: Creating incident response playbooks with platforms like Phantom or SOAR (Security Orchestration, Automation, and Response) to automate response actions during security incidents.
- Infrastructure as Code (IaC) Security:
- Project Example: Implementing security checks and policies within IaC templates (e.g., using AWS CloudFormation or Terraform) to ensure secure provisioning of cloud resources.
- Secure Software Development Lifecycle (SDLC):
- Project Example: Setting up a pipeline with secure coding practices, code reviews, and automated security testing integrated using tools like Jenkins, GitLab CI/CD, and security scanning tools.
- Continuous Monitoring and Threat Intelligence:
- Project Example: Integrating threat intelligence feeds with a security information and event management (SIEM) system to provide real-time alerts on emerging threats and indicators of compromise.
How to Implement DevSecOps?
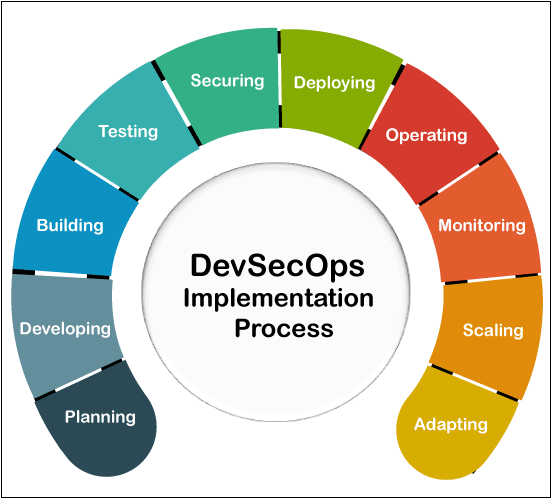
Implementing DevSecOps involves several key steps and best practices. Here’s a step-by-step guide, along with an example project to illustrate each stage:
- Cultural Shift and Education:
- Description: Foster a culture of collaboration and shared responsibility for security across development, operations, and security teams.
- Example Project: Organize workshops and training sessions on DevSecOps principles, emphasizing the importance of security in the development process.
- Risk Assessment and Threat Modeling:
- Description: Identify potential security risks and threats specific to your application and infrastructure.
- Example Project: Conduct a threat modeling session for a web application to identify potential vulnerabilities and prioritize them based on risk.
- Automated Security Testing:
- Description: Implement automated security testing tools to scan code and infrastructure for vulnerabilities.
- Example Project: Integrate a static code analysis tool like OWASP ZAP or SonarQube into your CI/CD pipeline to scan code for security issues.
- Container Security:
- Description: Implement security measures for containerized applications.
- Example Project: Set up a Docker image scanning tool like Clair to analyze container images for vulnerabilities before deployment.
- Continuous Compliance and Governance:
- Description: Automate compliance checks to ensure adherence to industry-specific regulations and organizational policies.
- Example Project: Utilize AWS Config rules or Chef InSpec to monitor and enforce compliance with AWS security best practices.
- Vulnerability Management:
- Description: Regularly scan networks and applications for known vulnerabilities and prioritize remediation efforts.
- Example Project: Use a vulnerability scanning tool like Nessus or Qualys to scan your network for known vulnerabilities and prioritize patching.
- Secrets Management:
- Description: Implement a system for securely storing and managing sensitive information used in applications.
- Example Project: Integrate HashiCorp Vault to securely manage and distribute API keys, passwords, and other secrets.
- Incident Response Automation:
- Description: Create automated incident response playbooks to streamline response actions during security incidents.
- Example Project: Use a platform like Phantom or SOAR to automate response actions based on predefined incident response procedures.
- Infrastructure as Code (IaC) Security:
- Description: Implement security checks and policies within IaC templates to ensure secure provisioning of cloud resources.
- Example Project: Incorporate security best practices and compliance checks directly into your Terraform scripts for provisioning AWS resources.
- Continuous Monitoring and Threat Intelligence:
- Description: Integrate threat intelligence feeds and continuously monitor for security threats and indicators of compromise.
- Example Project: Set up a SIEM solution like Splunk or ELK Stack, and integrate threat intelligence feeds to receive real-time alerts on emerging threats.
How to Get certified in DevSecOps?

- Visit the Website:
- Go to the official website of Devopsschool.com to explore the available courses and certifications related to DevSecOps.
- Browse DevSecOps Courses:
- Look for the specific DevSecOps course or certification program offered by Devopsschool.com. This may include options like “Certified DevSecOps Engineer” or similar titles.
- Review Course Details:
- Read through the course details, curriculum, prerequisites, and certification requirements provided on the course page. Make sure it aligns with your current skill level and career goals.
- Enroll in the Course:
- If you find a suitable DevSecOps course, follow the enrollment instructions provided on the website. This may involve creating an account, selecting a payment plan, and providing necessary information.
- Complete the Course Content:
- Work through the course materials, which may include video lectures, readings, assignments, and hands-on labs. Make sure to engage actively with the content to gain a comprehensive understanding.
- Participate in Hands-On Labs:
- Some DevSecOps courses may include practical exercises or labs to reinforce your learning. Participate in these activities to gain hands-on experience.
- Take Assessments and Exams:
- Most certification programs include assessments or exams to evaluate your understanding of the material. Be prepared to complete these assessments and achieve a passing score.
- Complete Projects:
- Some courses may require you to complete projects that demonstrate your ability to apply DevSecOps principles in real-world scenarios.
- Receive Certification:
- Once you successfully complete the course requirements, you will likely receive a digital certificate from Devopsschool.com attesting to your achievement in DevSecOps.
- Maintain and Renew Certification:
- Some certifications may have expiration dates, and you may need to complete additional requirements or renew the certification periodically.
- Visit the Website:
- Go to the official website of SCMGalaxy to explore the available courses and certifications related to DevSecOps.
- Browse DevSecOps Courses:
- Look for the specific DevSecOps course or certification program offered by SCMGalaxy. This may include options like “Certified DevSecOps Engineer” or similar titles.
- Review Course Details:
- Read through the course details, curriculum, prerequisites, and certification requirements provided on the course page. Make sure it aligns with your current skill level and career goals.
- Enroll in the Course:
- If you find a suitable DevSecOps course, follow the enrollment instructions provided on the website. This may involve creating an account, selecting a payment plan, and providing necessary information.
- Complete the Course Content:
- Work through the course materials, which may include video lectures, readings, assignments, and hands-on labs. Make sure to engage actively with the content to gain a comprehensive understanding.
- Participate in Hands-On Labs :
- Some DevSecOps courses may include practical exercises or labs to reinforce your learning. Participate in these activities to gain hands-on experience.
- Take Assessments and Exams:
- Most certification programs include assessments or exams to evaluate your understanding of the material. Be prepared to complete these assessments and achieve a passing score.
- Complete Projects:
- Some courses may require you to complete projects that demonstrate your ability to apply DevSecOps principles in real-world scenarios.
- Receive Certification:
- Once you successfully complete the course requirements, you will likely receive a digital certificate from SCMGalaxy attesting to your achievement in DevSecOps.
- Maintain and Renew Certification :
- Some certifications may have expiration dates, and you may need to complete additional requirements or renew the certification periodically.
- Visit the Website:
- Go to the official website of BestDevOps.com.
- Explore DevSecOps Certifications:
- Look for the specific DevSecOps certification programs offered by BestDevOps.com. This might include options like “Certified DevSecOps Engineer” or similar titles.
- Review Certification Details:
- Read through the certification details, curriculum, prerequisites, and requirements provided on the certification page. Ensure that it aligns with your current skills and career objectives.
- Enroll in the Certification Program:
- If you find a suitable DevSecOps certification, follow the enrollment instructions provided on the website. This might involve creating an account, selecting a payment plan, and providing necessary information.
- Complete the Certification Process:
- Work through the certification process, which may include training modules, assessments, exams, assignments, and practical exercises.
- Participate in Hands-On Labs (if applicable):
- Some DevSecOps certifications may include practical exercises or labs to reinforce your learning. Actively participate in these activities to gain hands-on experience.
- Pass Assessments and Exams:
- Most certification programs include assessments or exams to evaluate your understanding of the material. Be prepared to complete these assessments and achieve a passing score.
- Complete Projects (if applicable):
- Some certifications may require you to complete projects that demonstrate your ability to apply DevSecOps principles in real-world scenarios.
- Receive the Certification:
- Once you successfully complete the certification requirements, you will likely receive a digital certificate from BestDevOps.com or the certification provider, attesting to your achievement in DevSecOps.
- Maintain and Renew Certification (if applicable):
- Some certifications may have expiration dates, and you may need to complete additional requirements or renew the certification periodically.
By Cotocus.com
- Visit the Website:
- Go to the official website of Cotocus .
- Explore DevSecOps Certifications:
- Look for the specific DevSecOps certification programs offered by Cotocus. This might include options like “Certified DevSecOps Engineer” or similar titles.
- Review Certification Details:
- Read through the certification details, curriculum, prerequisites, and requirements provided on the certification page. Ensure that it aligns with your current skills and career objectives.
- Enroll in the Certification Program:
- If you find a suitable DevSecOps certification, follow the enrollment instructions provided on the website. This might involve creating an account, selecting a payment plan, and providing necessary information.
- Complete the Certification Process:
- Work through the certification process, which may include training modules, assessments, exams, assignments, and practical exercises.
- Participate in Hands-On Labs :
- Some DevSecOps certifications may include practical exercises or labs to reinforce your learning. Actively participate in these activities to gain hands-on experience.
- Pass Assessments and Exams:
- Most certification programs include assessments or exams to evaluate your understanding of the material. Be prepared to complete these assessments and achieve a passing score.
- Complete Projects :
- Some certifications may require you to complete projects that demonstrate your ability to apply DevSecOps principles in real-world scenarios.
- Receive the Certification:
- Once you successfully complete the certification requirements, you will likely receive a digital certificate from Cotocus or the certification provider, attesting to your achievement in DevSecOps.
- Maintain and Renew Certification :
- Some certifications may have expiration dates, and you may need to complete additional requirements or renew the certification periodically.
How to Learn DevSecOps?
Learning DevSecOps involves a combination of theoretical knowledge, hands-on experience, and practical application. Here’s a step-by-step guide to help you get started:
- Understand DevSecOps Concepts:
- Begin by familiarizing yourself with the fundamental concepts of DevSecOps, including its principles, practices, and the importance of integrating security into the DevOps process.
- Gain Knowledge of DevOps:
- Before diving into DevSecOps, it’s essential to have a solid understanding of DevOps practices. This includes knowledge of continuous integration, continuous delivery/deployment, automation, and collaboration.
- Learn Security Fundamentals:
- Develop a strong foundation in cybersecurity concepts, including secure coding practices, encryption, network security, authentication, authorization, and compliance standards.
- Explore Tools and Technologies:
- Familiarize yourself with the tools and technologies commonly used in DevSecOps, including version control systems, CI/CD pipelines, containerization platforms, and security scanning tools.
- Take Online Courses and Tutorials:
- Enroll in online courses or tutorials that specifically focus on DevSecOps. Platforms like Udemy, Coursera, edX, and Pluralsight offer a variety of courses on this topic.
- Read Books and Documentation:
- Consult books and official documentation related to DevSecOps. Look for resources that cover both DevOps practices and security principles.
- Participate in Workshops and Webinars:
- Attend workshops, webinars, and conferences related to DevSecOps. These events provide valuable insights, practical examples, and opportunities to network with professionals in the field.
- Set Up a Lab Environment:
- Create a lab environment where you can practice implementing DevSecOps principles. This could involve setting up a virtual machine or using cloud services to experiment with different tools and configurations.
- Hands-On Exercises and Projects:
- Engage in hands-on exercises and projects that involve integrating security into the development process. This could include tasks like setting up CI/CD pipelines with security checks, implementing secure coding practices, and conducting vulnerability assessments.
- Join Online Communities and Forums:
- Participate in online communities, forums, and discussion groups related to DevSecOps. Platforms like Reddit, Stack Overflow, and Dev.to are excellent places to ask questions and learn from experienced practitioners.
- Stay Updated with Industry Trends:
- Keep abreast of the latest developments in DevSecOps by following industry blogs, forums, and news sources. This will help you stay informed about emerging technologies and best practices.
- Obtain Certifications (Optional):
- Consider pursuing relevant certifications in DevSecOps. Certifications can validate your knowledge and skills and may be beneficial for career advancement.



