Limited Time Offer!
For Less Than the Cost of a Starbucks Coffee, Access All DevOpsSchool Videos on YouTube Unlimitedly.
Master DevOps, SRE, DevSecOps Skills!
What is Deception Technology?
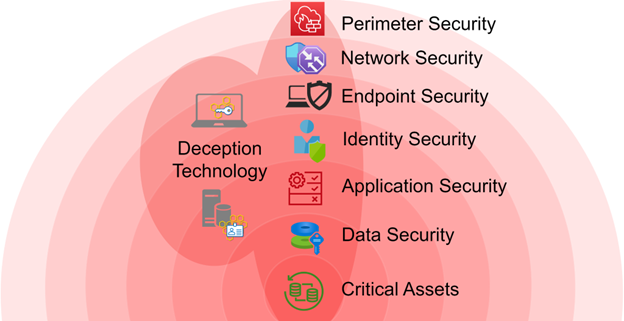
Deception Technology is a cutting-edge approach to cybersecurity that employs fake systems, data, and services to confuse and trap attackers. These decoys, often indistinguishable from real systems, are designed to mislead malicious actors into revealing their presence and intent. Once attackers interact with these traps, security teams are alerted, enabling them to respond promptly.
Unlike traditional cybersecurity measures, which are primarily defensive, deception technology takes an active approach by engaging attackers directly. This technology provides valuable insights into the methods and strategies used by cybercriminals, allowing organizations to stay ahead of potential threats.
Why Do We Need Deception Technology?
- Sophisticated Threat Landscape: As cyberattacks grow in complexity, traditional defenses like firewalls and antivirus programs often fail to detect advanced threats. Deception technology bridges this gap by identifying attackers early in their reconnaissance phase.
- Early Detection of Threats: By placing decoys across the network, deception technology can detect attackers before they breach critical assets, reducing the risk of data breaches and other damages.
- Minimized False Positives: Unlike other detection methods, interactions with deception tools are inherently malicious, eliminating false alarms and ensuring accurate threat identification.
- Proactive Threat Hunting: This technology doesn’t just wait for an attack; it actively lures attackers, allowing organizations to gather intelligence and anticipate future threats.
- Insider Threat Management: Deception technology can uncover malicious insiders or employees who unintentionally compromise security, providing a layer of protection against internal risks.
What Are the Advantages of Deception Technology?
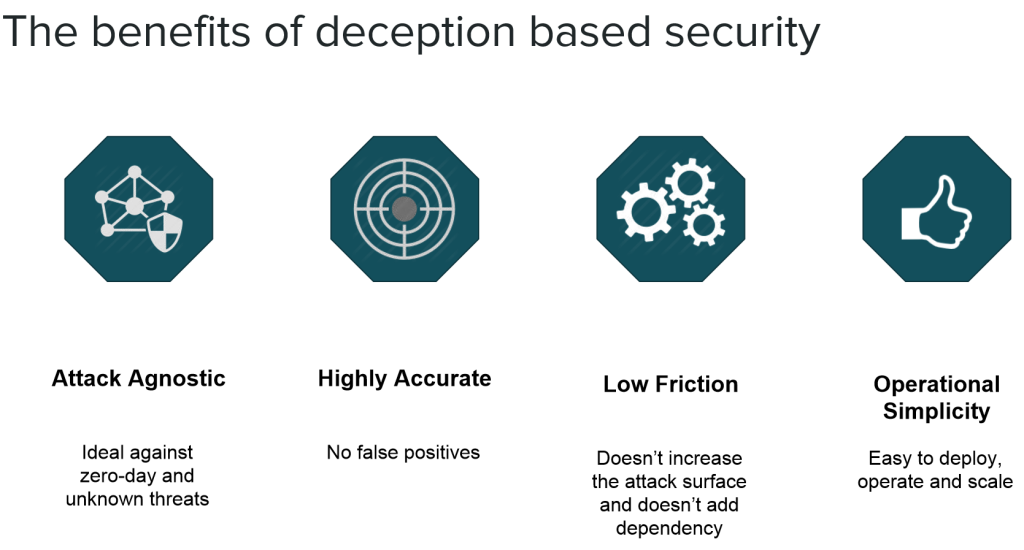
- Enhanced Threat Visibility: By monitoring interactions with decoys, organizations gain a clear picture of ongoing threats and attack vectors.
- Cost Efficiency: Deception solutions require minimal infrastructure changes, making them a cost-effective addition to existing security measures.
- Operational Continuity: Deception technology operates seamlessly in the background without disrupting legitimate business processes.
- Reduced Dwell Time: It significantly shortens the period attackers remain undetected within a network, minimizing potential damage.
- Forensic Intelligence: Captures detailed logs and activity patterns of attackers, aiding in investigations and strengthening incident response capabilities.
- Regulatory Compliance: Helps organizations meet industry standards and regulations by demonstrating robust threat detection and mitigation practices.
Key Features of Deception Technology
- Realistic Decoys: Mimics genuine systems, applications, and data to attract attackers.
- Scalability: Easily adaptable to networks of any size and complexity.
- Real-Time Alerts: Provides immediate notifications when a decoy is accessed.
- Automated Threat Analysis: Uses AI and machine learning to identify attack patterns and behaviors.
- Integration Capabilities: Seamlessly connects with existing security infrastructure, such as firewalls and SIEM (Security Information and Event Management) tools.
- Customizable Environments: Tailors decoys to resemble the organization’s actual network, enhancing their believability.
- Low Maintenance: Requires minimal manual intervention, thanks to automation.
Top 10 Use Cases of Deception Technology
- Detecting Advanced Persistent Threats (APTs): Identifies long-term, targeted cyberattacks designed to steal sensitive information or disrupt operations.
- Preventing Ransomware Attacks: Traps ransomware by directing it toward fake files and systems, protecting critical assets.
- Mitigating Insider Threats: Detects malicious or accidental insider activities, ensuring internal security.
- Securing IoT Devices: Protects connected devices by deploying decoy IoT endpoints that lure attackers.
- Industrial Control System Protection: Safeguards critical infrastructure in sectors like energy, manufacturing, and transportation.
- Endpoint Security: Monitors and detects lateral movements by attackers within an organization’s network.
- Cloud Environment Security: Deploys decoys in cloud environments to detect unauthorized access and malicious activities.
- Zero-Day Threat Detection: Identifies and analyzes new, previously unknown vulnerabilities exploited by attackers.
- Cyber Threat Intelligence Gathering: Collects valuable data on attacker methodologies and tools, enabling organizations to bolster their defenses.
- Compliance Support: Helps organizations identify vulnerabilities and implement security measures required to meet regulatory standards.
How to Implement Deception Technology
- Assess Your Network:
- Conduct a thorough analysis to identify critical assets and potential vulnerabilities.
- Understand your threat landscape and tailor the deception strategy accordingly.
- Define Clear Objectives:
- Decide what you aim to achieve, such as early detection, insider threat management, or compliance.
- Deploy Decoys Strategically:
- Place decoys in locations likely to attract attackers, such as unused IP addresses, shared directories, or specific server environments.
- Ensure decoys mimic real systems closely to make them believable.
- Integrate with Existing Security Tools:
- Connect deception technology with firewalls, intrusion detection systems, and SIEM platforms for comprehensive coverage.
- Monitor and Analyze:
- Continuously monitor decoys for unauthorized access.
- Use logs and alerts to analyze attacker behavior and improve defenses.
- Leverage Automation and AI:
- Automate threat detection and analysis to reduce manual efforts.
- Use machine learning to identify sophisticated attack patterns.
- Test and Optimize:
- Regularly test the effectiveness of your decoys.
- Update and optimize them to reflect changes in your network and threat landscape.
- Train Your Team:
- Educate security teams on how to use deception technology effectively.
- Include deception strategies in incident response plans.
- Develop Incident Response Plans:
- Use the intelligence gathered to create actionable response strategies for potential threats.
- Scale and Evolve:
- Periodically review your deception deployment and scale it to meet evolving security needs.



